
Around 40% of ethical hackers recently surveyed by the SANS Institute said they can break into most environments they test, if not all. Nearly 60% said they need five hours or less to break into a corporate environment once they identify a weakness.
The SANS ethical hacking survey , done in partnership with security firm Bishop Fox, is the first of its kind and collected responses from over 300 ethical hackers working in different roles inside organizations, with different levels of experience and specializations in different areas of ...
Brazilian Prilex Hackers Resurfaced With Sophisticated Point-of-Sale Malware
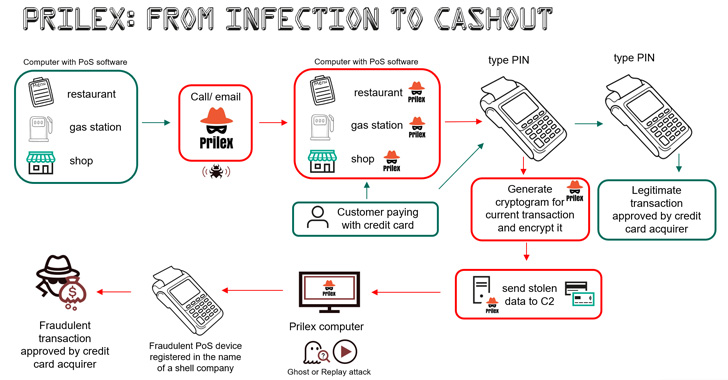
A Brazilian threat actor known as Prilex has resurfaced after a year-long operational hiatus with an advanced and complex malware to steal money by means of fraudulent transactions.
"The Prilex group has shown a high level of knowledge about credit and debit card transactions, and how software used for payment processing works," Kaspersky researchers said .
Mystery Hackers Are 'Hyperjacking' Targets for Insidious Spying | WIRED

For decades, virtualization software has offered a way to vastly multiply computers' efficiency, hosting entire collections of computers as "virtual machines" on just one physical machine.
Today, Google-owned security firm Mandiant and virtualization firm VMware jointly published warnings that a sophisticated hacker group has been installing backdoors in VMware's virtualization software on multiple targets' networks as part of an apparent espionage campaign.
How hobbyist hackers are preserving Pokémon's past—and shaping its future | Ars Technica

Earlier this year, Pokémon Legends: Arceus reinvigorated developer Game Freak's iconic series by shaking up a formula that had gone largely unchanged for more than 25 years. But that recent bout of experimentation doesn't diminish just how long the Poké-formula has remained mostly static.
Hackers Aid Protests Against Iranian Government with Proxies, Leaks and Hacks

The company said it has also witnessed sharing of proxies and open VPN servers to get around censorship and reports on the internet status in the country, with one group helping the anti-government demonstrators access social media sites.
Chief among them is a Telegram channel called Official Atlas Intelligence Group (AIG) that's primarily focused on publishing data associated with government officials as well as maps of prominent locations.
Microsoft: Lazarus hackers are weaponizing open-source software

Microsoft says the North Korean-sponsored Lazarus threat group is trojanizing legitimate open-source software and using it to backdoor organizations in many industry sectors, such as technology, defense, and media entertainment.
The list of open-source software weaponized by Lazarus state hackers to deploy the BLINDINGCAN (aka ZetaNile) backdoor includes PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer.
Department of Defense Forks Over $110K to Hackers Who Discovered 349 Bugs | PCMag

The US Department of Defense (DoD) has paid out $110,000 in bounties and bonuses to ethical hackers who discovered 349 "actionable" vulnerabilities on its networks.
As The Record reports (Opens in a new window) , the vulnerabilities were discovered at a week-long " Hack U.S. (Opens in a new window) " event held in July through a partnership with Hackerone.
Hackers Experimenting with Deploying Destructive Malware | Robinson+Cole Data Privacy + Security ...

The newest trend for hackers is to develop and launch cyber-attacks that deploy destructive malware.
at least one ransomware group is testing “data destruction” attacks.
The suspected ransomware group is BlackCat, which might be a rebrand of BlackMatter, “which in turn was a rebrand of Darkside, the ransomware operation behind the Colonial Pipeline attack.”
Hackers now sharing cracked Brute Ratel post-exploitation kit online

The Brute Ratel post-exploitation toolkit has been cracked and is now being shared for free across Russian-speaking and English-speaking hacking communities.
For those unfamiliar with Brute Ratel C4 (BRC4), it is a post-exploitation toolkit created by Chetan Nayak, an ex-red teamer at Mandiant and CrowdStrike.
Army of the Alien Monkeys
Earth is nice. We want it.
We welcome your submission to us.
No comments:
Post a Comment