While this may indicate the attackers are in Russia, there is the possibility that it is a false flag operation attempting to obfuscate the attack's true origins.
The campaign is part of a trend of annual tax-related scams that ramp up at the beginning of each year. The Internal Revenue Service (IRS) identified $5.7 billion in tax fraud schemes last year, more than twice the amount reported in 2021.
Pro-Russian hackers target elected US officials supporting Ukraine | Ars Technica

Raggi declined to identify the targets except to say they included elected US officials and staffers at the federal government level as well as European entities.
PCIe For Hackers: Extracting The Most | Hackaday
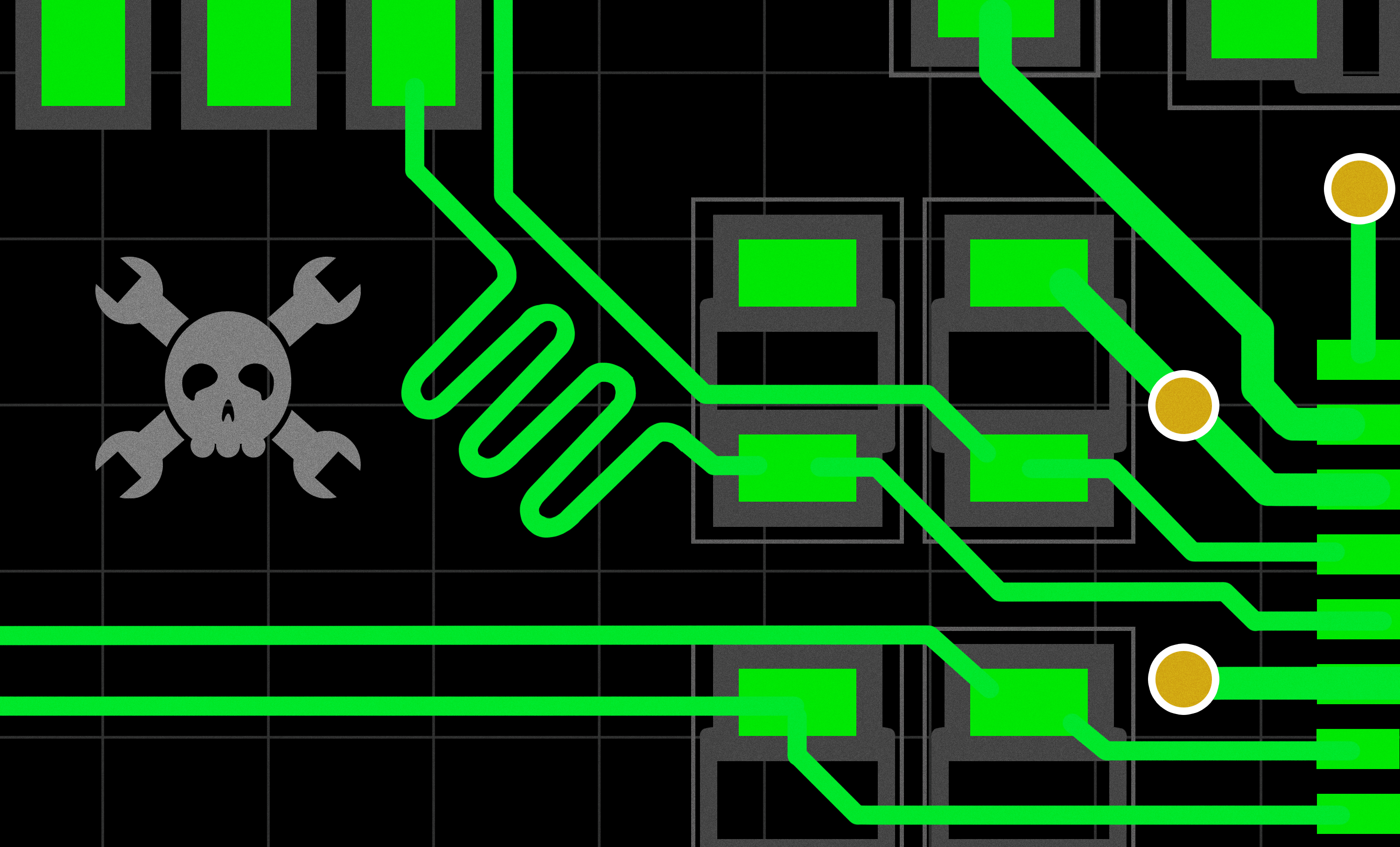
So, you now know the basics of approaching PCIe, and perhaps you have a PCIe-related goal in mind.
Now, there’s an alternative, and it’s PCIe switches – these are hefty chips which present a PCIe device interface to your host, and multiple PCIe host interfaces for all your devices; you could compare them to Ethernet switches in terms of how they work, except that lanes of a ...
5 Key Ways A Hacker Approach Can Benefit Managers

Some say the idea of a manager thinking like a hacker brings a different type of innovation to the ... [+] workplace.
Paulo Savaget, associate professor at the University of Oxford believes managers can be more ... [+] efficient if they think like hackers.
How to cut the line on increasingly phishy hackers this tax season | Security Magazine

So, as the 2023 tax season continues, how can CISOs bolster their security posture amidst the accelerated use of personal devices among employees and the identity-based cyberattacks that follow suit?
Through the adoption of modern, zero-trust defense strategies, enterprises can reduce their high-risk identity attack surface and maintain full visibility and control to pinpoint access for every employee to every device, in any location. Let's dive into this topic further.
1/3 Researchers warn of a hacker group called TACTICAL#OCTOPUS using tax-related #phishing scams to spread #malware… https://t.co/x548n5TnhN TheRecord_Media (from The Internet) Sun Apr 02 17:59:04 +0000 2023

No comments:
Post a Comment