It happens all the time: hackers take control of Facebook accounts and their rightful owners can’t log in to get them back.
To keep this from happening to you, take a minute to set up a little known Facebook feature called Trusted Contacts to protect you.
That’s all there is to it. I also highly recommend setting up two-factor authentication for your Facebook account. This will verify all logins to your account with special code texted to your phone.
Was Braman Motors target of hackers demanding ransom money? Employee says it's true
:strip_exif(true):strip_icc(true):no_upscale(true):quality(65)/d1vhqlrjc8h82r.cloudfront.net/04-16-2021/t_d44afca9ee1d46409984a94e53a43ce9_name_image.jpg)
MIAMI, Fla. – Sources have told Local 10 that Braman Motors was the target of a sophisticated cyberattack, but the company is calling what they are dealing with a "network outage."
The employee, who wanted to remain anonymous, said a notice flashed on some of Braman's computers. "The whole system at Braman crashed and we got a ransom note from the hackers. They took the whole system out and they are asking for money."
Medtronic partners with cybersecurity startup Sternum to protect its pacemakers from hackers
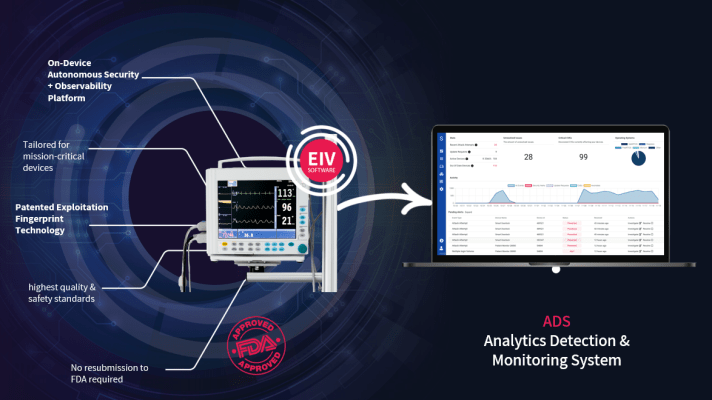
If you think cyberattacks are scary, what if those attacks were directed at your cardiac pacemaker? Medtronic, a medical device company, has been in hot water over the last couple of years because its pacemakers were getting hacked through their internet-based software updating systems. But in a new partnership with Sternum , an IoT cybersecurity startup based in Israel, Medtronic has focused on resolving the issue.
The problem was not with the medical devices themselves, but with the remote systems used to update the devices. Medtronic's previous solution was to disconnect the devices from the internet, which in and of itself can cause other issues to arise.
U.S. Exposes Hackers' Helpers to Punish Russian Attacks
(Bloomberg) -- In punishing Russian hacks and election meddling, the Biden administration on Thursday revealed new details about Russian intelligence's vast disinformation and cyber-operations, including the names of companies that allegedly help facilitate cyber-attacks and websites accused of spreading false claims to damage the U.S.
The information release is designed partly to damage Russian intelligence services by blowing the cover of its support network, including companies that provide essential services and, in one case, the location of a technology park near the Black Sea used by spies for Russian's military intelligence directorate, the GRU.
SolarWinds: US and UK blame Russian intelligence service hackers for major cyberattack | ZDNet

Hackers working for the Russian foreign intelligence service are behind the SolarWinds attack, cyber-espionage campaigns targeting COVID-19 research facilities and more, according to the United States and the United Kingdom.
Now the US has publicly attributed the SolarWinds attacks to Russian Foreign Intelligence Service (SVR) actors -- also known as APT29, Cozy Bear, and The Dukes by cybersecurity researchers -- along with additional campaigns, including malware attacks targeting facilities behind COVID-19 vaccine development.
How Russia Used SolarWinds To Hack Microsoft, Intel, Pentagon, Other Networks : NPR

Hackers believed to be directed by the Russian intelligence service, the SVR, used that routine software update to slip malicious code into Orion's software and then used it as a vehicle for a massive cyberattack against America.
On Thursday, the Biden administration announced a roster of tough sanctions against Russia as part of what it characterized as the "seen and unseen" response to the SolarWinds breach.
For that reason, Ramakrishna figures the Russians successfully compromised about 100 companies and about a dozen government agencies. The companies included Microsoft, Intel and Cisco; the list of federal agencies so far includes the Treasury, Justice and Energy departments and the Pentagon.
Cybersecurity training lags, while hackers capitalize on the pandemic | 2021-04-14 | Security

<a href="https://www.freepik.com/photos/background">Background photo created by rawpixel.com - www.freepik.com</a>
Recently, TalentLMS partnered with Kenna Security to survey 1,200 employees on their cybersecurity habits, knowledge of best practices, and ability to recognize security threats. Here are some of the staggering results that offer some explanation as to why cybercrime has grown into such a lucrative business:
These staggering results lead to the conclusion that simply having a cybersecurity training program in place isn't enough. The majority of employees also report that their companies have implemented the correct fundamental safeguards that provide essential protection from cybersecurity threats:
Kick Hackers to the Curb With This Hardware To Protect Your Privacy

If you're still surfing the net without proper protection of your information, you're just asking for a hack or for your data to be jacked -- it's time to get your house in your order.
With Winston ... you're just shelling out a one-time payment of about $179. Good deal , ain't it?
The Cybersecurity 202: The FBI launched an operation to wipe out hacker access to hundreds of U.S.

The Justice Department announced yesterday it launched an operation to eliminate back doors into hundreds of U.S.-based servers exposed by a Microsoft Exchange vulnerability identified by the company earlier this year.
"Today's court-authorized removal of the malicious web shells demonstrates the Department's commitment to disrupt hacking activity using all of our legal tools, not just prosecutions," Assistant Attorney General John C. Demers of the Justice Department's National Security Division said in a release. " There's no doubt that more work remains to be done, but let there also be no doubt that the Department is committed to playing its integral and necessary role in such efforts."


No comments:
Post a Comment