
This has the drawback of being an active attack, with that laser beam having to illuminate the surface and so being open to easy detection. The newly reported surveillance methodology, however, is passive in nature.
To pull off this privacy-busting attack 'simply' requires the use of an electro-optical sensor attached to a telescope. Once this is pointed at the target power LED, from distances of up to 100 feet away, the optical signal can be sampled.
In a first for Maine, ransomware hackers hit 2 public wastewater plants

The Department of Environmental Protection has warned municipalities and water-sector professionals to be on alert after two recent ransomware intrusions, believed to be the first on wastewater systems in Maine.
The attacks occurred in Limestone and Mount Desert Island, said Judy Bruenjes, a wastewater technical assistance engineer for the DEP.
Explainer: How hackers stole and returned $600 mln in tokens from Poly Network | Reuters
/cloudfront-us-east-2.images.arcpublishing.com/reuters/NBRKXEPTDNJMLIR6MHRGI6QLYM.jpg)
Representations of the virtual currency stand on a motherboard in this picture illustration taken May 20, 2021. REUTERS/Dado Ruvic/Illustration
WASHINGTON, Aug 12 (Reuters) - Hackers pulled off the biggest ever cryptocurrency heist on Tuesday, stealing more than $600 million in digital coins from token-swapping platform Poly Network, only to return nearly all the assets less than 48 hours later, the company said. [nL1N2PJ21E]
5 Most Ridiculous Hackers In Movie History (& 5 That Were Actually Believable)

Hacking in films has been a mainstay since the '90s when the internet got first introduced . In most cases, the hacker is some god-like individual who can get into any top secret file they want in a matter of minutes. In reality, there's quite a bit more to it than that.
At its worst, it produces moments that take even the average viewer out of a movie . No one likes having some instant 'I Win' button because it marginalizes the rest of the plot . Thankfully, there have been a few movies that treat the profession with plenty of respect.
Bloomberg - Are you a robot?
London court orders Binance to trace cryptocurrency hackers | Reuters
/cloudfront-us-east-2.images.arcpublishing.com/reuters/CGHJLXVFVVN6NM6BUAFK3KRIYI.jpg)
A representation of cryptocurrency Binance is seen in this illustration taken August 6, 2021. REUTERS/Dado Ruvic/Illustration
In a judgment made public this week, a High Court judge granted requests by artificial intelligence (AI) company Fetch.ai for Binance to take steps to identify the hackers and track and seize the assets.
Apex Legends players concerned as data shows Warzone streamers are bringing hackers - Dexerto

With drama surrounding Call of Duty’s Warzone battle royale, Apex Legends has been getting a lot more love from major Twitch streamers. Unfortunately, players have dug up data which suggests that hackers are switching over as well.
The most prominent problem with Warzone over the past few months has been the overwhelming amount of hackers found in higher-skilled lobbies. Apex, a game less-known for hacking issues, has therefore become a refuge of sorts for frustrated Warzone players .
Ransomware in Healthcare: The Costly Reality of Withstanding Hackers

This isn't a rhetorical question, even if it may be difficult to come up with a direct answer. After all, between 1960 and 2018, healthcare increased as a percentage of GDP from a modest 5 percent to more than triple that at almost 18 percent.
The rise in healthcare's share of GDP would be less of a concern if it were accompanied by similar growth in productivity, i.e., caring for more people so that per capita healthcare costs grew at a much slower pace, if at all.
Hackers Spotted Using Morse Code in Phishing Attacks to Evade Detection
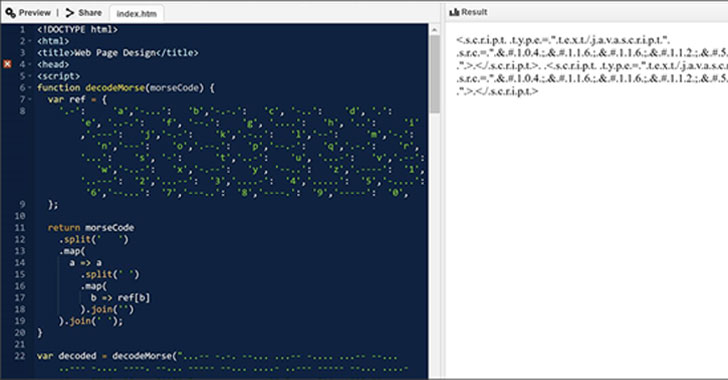
Microsoft has disclosed details of an evasive year-long social engineering campaign wherein the operators kept changing their obfuscation and encryption mechanisms every 37 days on average, including relying on Morse code, in an attempt to cover their tracks and surreptitiously harvest user
Microsoft likened the attachment to a "jigsaw puzzle," noting that individual parts of the HTML file are designed to appear innocuous and slip past endpoint security software, only to reveal its true colors when these segments are decoded and assembled together.
Global ... Why it’s so hard for the U.S.

Regulations on cryptocurrency vary widely around the world, and it won't be easy for the U.S. to alter that dynamic as it seeks to neutralize hackers' money flow.
The Bitcoin logo appears on the display screen of a crypto currency ATM at the Smoker's Choice store in Salem, N.H on Feb. 9, 2021. | AP Photo/Charles Krupa, File
Happening on Twitter
How Hackers Use Power LEDs To Spy On Conversations 100 Feet Away https://t.co/xweQAtuT11 Forbes (from New York, NY) Sun Aug 15 11:40:10 +0000 2021
How hackers use power LEDs to spy on conversations 100 feet away: https://t.co/FlFAwATjWx https://t.co/tfoEe3OwxK Forbes (from New York, NY) Sun Aug 15 14:40:03 +0000 2021
New by me @Forbes: How to listen in on audio conversations, up to 100 feet away, by watching miniscule power LED fl… https://t.co/JOeBQQRzP1 happygeek (from West Yorkshire, UK) Sun Aug 15 11:06:45 +0000 2021



No comments:
Post a Comment