The gap between IT security professionals and line of business managers' understanding of risk is at the heart of many issues, according to Ponemon Institute research released this week.
Sonrai Security said it is launching cloud workload protection capabilities in its Sonrai Dig platform to safeguard users in the public cloud, according to VentureBeat.
Hackers swipe $625 million from a blockchain platform, raising security concerns in the cryptosphere

The breach highlights the compromises that come with high privacy and low regulation in the financial realm
Hackers stole $625 million in cryptocurrency in an intrepid attack on Axie Infinity, a video game in which players collect and mint NFTs which represent axolotl-inspired digital pets. Vietnamese studio Sky Mavis, the maker of the blockchain game, will be unable to recover the funds.
Why the Lapsus$ teen hackers stole all that data, according to a former teen hacker.

Teens hacking into large corporations are once again in the news. This time, a group of teens in the UK have taken responsibility for a series of major hacks of big tech companies like Microsoft, Nvidia, and Okta over the last month.
Two suspected members of the group, ages 16 and 17 , are appearing before the Highbury Corner Magistrates' Court in the UK on Friday on charges of a variety of cybercrimes connected to their alleged activities with the hacking group.
Yes, longer passwords better protect your account from hackers | cbs8.com
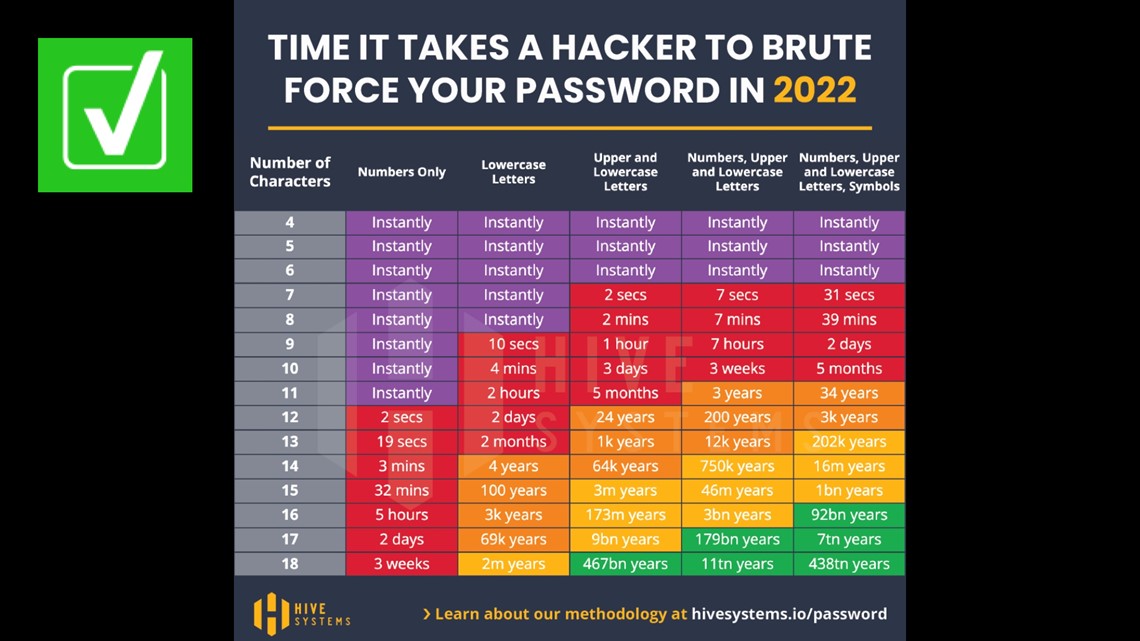
if it's 18 characters with numbers, upper and lower case letters, as well as symbols, it would take 438 trillion years.
CBS 8 spoke with Alex Nette, CEO and Co-Founder of Hive Systems , and James Lee, Chief Operating Officer of the Identity Theft Resource Center , a national non-profit.
Russian Hackers Target NATO And Eastern European Militaries, Google Says

A participant sits with a laptop computer as he attends the annual Chaos Communication Congress of ... [+] the Chaos Computer Club at the Berlin Congress Center on December 28, 2010 in Berlin, Germany.
A Russian-based hacking group known as COLDRIVER or Callisto has targeted one of NATO's Centres of Excellence military training organizations, as well as multiple unnamed Eastern European nations, Google said in a TAG blog Wednesday.
Chinese Hackers Target VMware Horizon Servers with Log4Shell to Deploy Rootkit
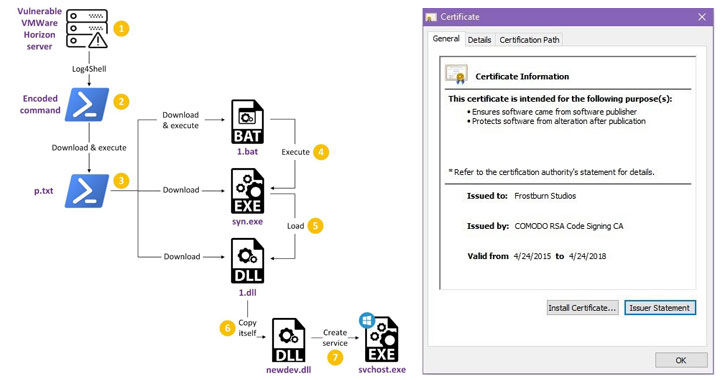
A Chinese advanced persistent threat tracked as Deep Panda has been observed exploiting the Log4Shell vulnerability in VMware Horizon servers to deploy a backdoor and a novel rootkit on infected machines with the goal of stealing sensitive data.
"The nature of targeting was opportunistic insofar that multiple infections in several countries and various sectors occurred on the same dates," said Rotem Sde-Or and Eliran Voronovitch, researchers with Fortinet's FortiGuard Labs, in a report released this week.
Critical Bugs in Rockwell PLC Could Allow Hackers to Implant Malicious Code
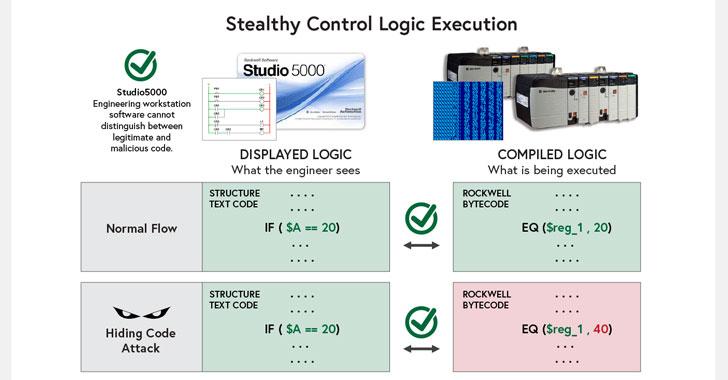
Two new security vulnerabilities have been disclosed in Rockwell Automation's programmable logic controllers ( PLCs ) and engineering workstation software that could be exploited by an attacker to inject malicious code on affected systems and stealthily modify automation processes.
Hackers duped Apple, Meta into handing over user data: report https://t.co/amnl1wHNCJ FoxNews (from U.S.A.) Thu Mar 31 22:30:00 +0000 2022
Apple and Meta duped into giving away customer data https://t.co/rQZusg7wyX RT_com Thu Mar 31 00:50:10 +0000 2022
Child hacker gang posing as cops 'duped' Meta and Apple into handing over user data https://t.co/S7iPJit3i2 MailOnline Thu Mar 31 06:02:15 +0000 2022

No comments:
Post a Comment