
Hackers have been spotted infiltrating Microsoft Teams meetings with the goal of circulating malware to unsuspecting users.
Once inside a meeting, hackers will drop a malicious executable file that pretends to be a legitimate program called “User Centric." If a user installs it, the Trojan program will drop malicious DLL files on the PC, which can allow the hacker to remotely hijack the system.
Hackers Had Access to Red Cross Network for 70 Days | SecurityWeek.Com
One month after disclosing a data breach that affected roughly 515,000 people, the International Committee of the Red Cross (ICRC) announced that the hackers had access to its network for 70 days before the attack was discovered.
The attackers gained access to the Red Cross network on November 9, 2021, by exploiting CVE-2021-40539 , a critical-severity authentication bypass flaw in Zoho's ManageEngine ADSelfService Plus, ICRC explains in an updated FAQ .
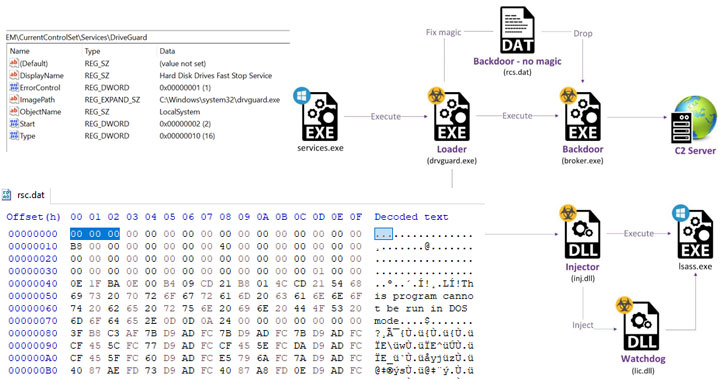
Moses Staff Hackers Targeting Israeli Organizations for Cyber Espionage
First publicly documented in late 2021, Moses Staff is believed to be sponsored by the Iranian government, with attacks reported against entities in Israel, Italy, India, Germany, Chile, Turkey, the U.A.E., and the U.S.
Earlier this month, the hacker collective was observed incorporating a previously undocumented remote access trojan (RAT) called " StrifeWater " that masquerades as the Windows Calculator app to evade detection.
How Ethical Hacking Can Stop Hackers

You may have heard of ethical hacking or “white-hat” hacking. It’s an increasingly widely utilized way to help companies uncover vulnerabilities that hackers may exploit later.
Ethical hacking occurs when a person receives permission to attempt to break into an app or system or steal data. The individual mimics the efforts a malicious hacker would likely make. They then provide a report of identified vulnerabilities and suggested steps for remediation.
Devious hackers are using NFT hype to hijack your PC and webcam | ZDNet

Danny Palmer is a senior reporter at ZDNet. Based in London, he writes about issues including cybersecurity, hacking and malware threats.
BitRAT is a remote access trojan (RAT) that first emerged for sale in underground forums in August 2020. What makes it notable is it can bypass User Account Control (UAC), a Windows feature that helps to prevent unauthorised changes to the operating system.
Cybercrime focus of Justice Department crackdown on global hackers

In a speech to attendees at the annual Munich Security Conference, Deputy Attorney General Lisa Monaco unveiled several new initiatives by the Justice Department and FBI that she said will speed up their transformations into the kind of high-tech law enforcement agencies required to go after
"Ransomware and digital extortion – like many other crimes that are fueled by cryptocurrency – only work if the bad guys get paid,which means we have to bust their business model," Monaco said.
Canada Freedom Convoy: GiveSendGo demands FBI probe hackers, alleges 'highly

The executive director of the Canadian Civil Liberties Association said Trudeau's 'emergency' invoked too much power that was unwarranted for the situation.
The notorious Canadian hacker Aubrey Cottle, known as Kirtaner, seemed to take partial credit for the cyberattack on the Freedom Convoy 2022's campaign in a TikTok video circulating online.
Hackers to face 25 years in jail for cyber attacks on Australia's national infrastructure |

The bill also makes adjustments to the law governing unauthorised access to, or the modification of, restricted data and unauthorised impairment of data held on a computer disk. In this case the maximum jail term will increase from two years to five years.
"Although a positive step in the fight against cybercriminals, this deterrent will by no means be the end of ransomware in Australia," said Camellia Chan, CEO and Founder of X-PHY. "It is imperative that organisations do not rest on their laurels despite tougher punishments for criminals.

No comments:
Post a Comment