
With tech to hunt down hackers, cryptocurrency heists just got harder | Business Standard News

Ringo Presents Soul Hackers 2 June 26th Daily Demon; Milky Frost - Noisy Pixel
![]()
Atlus Japan has begun a new series on its Youtube channel where the protagonist of the upcoming Soul Hackers 2 , Ringo, introduces demons that will appear in the title.
This one-hundredth-and-ninth video's contents have been translated by our team's Ryuji , viewable below:
Hackers Are Still Exploiting Log4Shell Vulnerability, Warns CISA - Security Boulevard

CISA and US Coast Guard Cyber Command (CGCYBER) warned that nation-state hackers are still exploiting Log4Shell, specifically targeting unpatched, internet-facing VMware Horizon and Unified Access Gateway servers.
"As part of this exploitation, suspected APT actors implanted loader malware on compromised systems with embedded executables enabling remote command and control (C2)," alerted CISA.
Stronger Security for Smart Devices To Efficiently Protect Against Powerful Hacker Attacks

By Adam Zewe, Massachusetts Institute of Technology June 26, 2022 MIT engineers demonstrated that analog-to-digital converters in smart devices are vulnerable to power and electromagnetic side-channel attacks that hackers use to "eavesdrop" on devices and steal secret information.
Engineers demonstrate two security methods that efficiently protect analog-to-digital converters from powerful attacks that aim to steal user data.
What Is Fuzzing in Cybersecurity?

Software vulnerabilities are a significant problem in cybersecurity. They allow software products to be attacked and when those products are connected to otherwise secure networks, they can provide an entry point for hackers.
All professional software products are thoroughly tested prior to release. Unfortunately, vulnerabilities are still a common occurrence. One way to find additional vulnerabilities is to use a software testing technique known as fuzzing.
Jacuzzis could be hacked and turned into 'hot, stinky soup'
Hot tub maker Jacuzzi is in hot water after a cybersecurity researcher said he found vulnerabilities in its app that risk exposing user data and let hackers remotely control tubs.
Jacuzzi's "SmartTub" app — which lets users control hot tubs' temperature, lighting and jets from their phones — is vulnerable to hackers, according to a cybersecurity researcher who publishes under the pseudonym EatonWorks.
Russian Hackers May Have Blown Up A Massive Natural Gas Facility In Texas: REPORT | The Daily Caller

A Russian state-backed cybercrime group may be behind an explosion at a Quintana Island, Texas, natural gas plant and transfer point on June 8, Washington Examiner writer Tom Rogan reported Tuesday.
Would-be attackers escalated intelligence gathering efforts on Texas-based liquefied natural gas (LNG) company Freeport LNG near the time of Russia’s invasion of Ukraine, according to Rogan.
Want A Break From Hardware Hacking? Try Bitburner | Hackaday
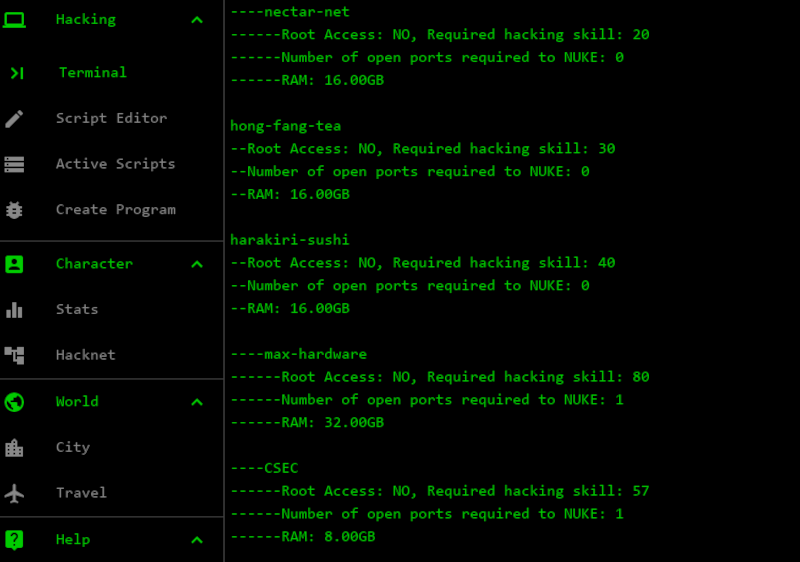
If you ever mention to a normal person that you’re a hacker, and they might ask you if you can do something nefarious.
We did think it was bad form that the tutorial admonished us for not entering the commands it wanted us to. What kind of hacker wouldn’t try something else? Anyway, it’s probably a better diversion than whatever Facebook or phone game your friends are wasting time with.
TechDay - 3 Cybersecurity Tips You Should Know
When sensitive data is leaked, it circulates indefinitely among hackers. As a result, it gives them access to credit cards, bank accounts, and customer and employee records, to name a few.
Data might be more commonly associated with marketing and forecasting, but it can also be leveraged to improve your cybersecurity efforts.
Quincy Jones would talk to every person at a book signing and leave a personalized note even if it took him until 3… https://t.co/kGSPZ1CNkR gregisenberg (from 30,000 people read my emails →) Sat Jun 25 16:34:46 +0000 2022
Did you remember to get dad a new, personalized number 3 Robertson head non-slip screwdriver for #FathersDay? https://t.co/LWOCugKj00 MitchellsMovie Sun Jun 19 17:00:00 +0000 2022
SOLD OUT OF BASE CD BUNDLES!!! 😱😱😱😱 stock remains of the MINI BUNDLES however, so you haven't fully lost your chanc… https://t.co/Tt9JR6xxcB LeeandLie (from in the multiverse ) Fri Jun 17 21:36:27 +0000 2022
System Unknown NFT Collection
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/systemunknown
Check out the System Unknown artwork. Click here.

No comments:
Post a Comment