The primary targets of the intrusions from May to October 2022 included counties in the Asia Pacific region such as Myanmar, Australia, the Philippines, Japan, and Taiwan, cybersecurity firm Trend Micro said in a Friday report.
Mustang Panda, also called Bronze President, Earth Preta, HoneyMyte, and Red Lich, is a China-based espionage actor believed to be active since at least July 2018. The group is known for its use of malware such as China Chopper and PlugX to collect data from compromised environments.
Microsoft Warns of Hackers Using Google Ads to Distribute Royal Ransomware

A developing threat activity cluster has been found using Google Ads in one of its campaigns to distribute various post-compromise payloads, including the recently discovered Royal ransomware .
Microsoft, which spotted the updated malware delivery method in late October 2022, is tracking the group under the name DEV-0569 .
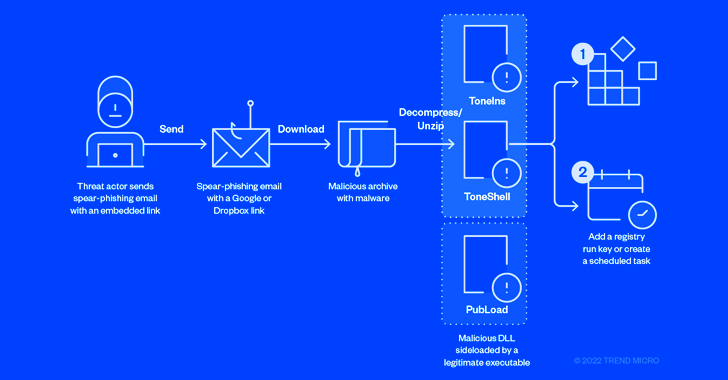
Chinese hackers use Google Drive to drop malware on govt networks

State-backed Chinese hackers launched a spearphishing campaign to deliver custom malware stored in Google Drive to government, research, and academic organizations worldwide.
The attacks have been observed between March and October 2022 and researchers attributed it to the cyber espionage group Mustang Panda (Bronze President, TA416).
Microsoft: Hackers are using this 'concerning' tactic to dodge multi-factor authentication | ZDNET

Three years ago, attacks on multi-factor authentication (MFA) were so rare that Microsoft didn't have decent statistics on them , largely because few organisations had enabled MFA.
Moreover, Microsoft warns that token theft is dangerous because it doesn't require high technical skills, detection is difficult and, because the technique has only recently seen an uptick, few organisations have mitigations in place.
Hackers Aren't The Only Unseen Enemy Behind Cyber Attacks

Translating cybersecurity risks into board-friendly language is an art. Here's how executives can educate their board members regarding cybersecurity risks and the need to incorporate stringent security measures.
The booming numbers of cybersecurity threats have compelled every C-suite executive and board members to pay closer attention to their cybersecurity hygiene. However, they don't share the same lens while watching their information security posture. And here's where a disconnect arises.
Hackers target your holiday shopping with new phishing scam | Digital Trends

The attack was identified by Akamai and was recently reported on Scam Watcher , where screenshots were also shared, as noted by Bleeping Computer . The carrot that's dangled is a free gift that is nice, but not so expensive as to be unbelievable.
For those wary of such gifts, scrolling down a bit reveals fake testimonials from people who have supposedly finished the survey and received their reward with no trouble whatsoever. If you were tempted by the gift, this might give you enough reassurance to proceed.
Shoppers Warned Stay Alert this Black Friday as Hackers Renew Efforts - Infosecurity Magazine

Shoppers should stay alert on Black Friday as hackers launch new scams in the lead-up to the event.
Check Point Research ( CPR ) said the team has already observed a sharp increase in shopping-related phishing scams, with threat actors imitating well-known brands.
The feds warn that hackers could hold Midwestern harvests hostage with ransomware | HPPR

"Cyber criminals know this," Omaha-based FBI Special Agent Eugene Kowel said. "They're very savvy, and they know that hacking into U.S. agriculture can yield a big payday."
The stakes rise even higher during fall's harvest season, when farmers come under pressure to get crops out of fields quickly and can be extorted to pay a ransom if it means getting back to work.
8 Questions We Still Have After The End Of Soul Hackers 2

Forming a party and going after a giant threat to the world isn't new for JRPGs, and for Soul Hackers 2 , at least on the surface, it seems as though it's just the same.
Bubbling under the surface, though, are themes of technology reliance, empathy, and the concept of true free will. And although these elements of the story are fine and carry the story through, the world leaves us with more questions than answers. Be warned: spoilers abound.
FBI Targeted by Russian Hackers in Latest String of Attacks Against U.S.

It is increasingly common for hackers and other cyber criminals to tout their abilities on social media, but this week a Russian hacking collective was a bit more brazen than usual.
The type of attack was believed to be a distributed denial-of-service (DDoS), which is a malicious attempt to disrupt normal traffic to a website.
Chinese Mustang Panda hackers have been linked to a spate of spear-phishing attacks targeting governments, educatio… https://t.co/CXd3Do9p9T TheHackersNews (from The Internet) Sat Nov 19 14:21:00 +0000 2022
Army of the Alien Monkeys
Earth is nice. We want it.
We welcome your submission to us.

No comments:
Post a Comment