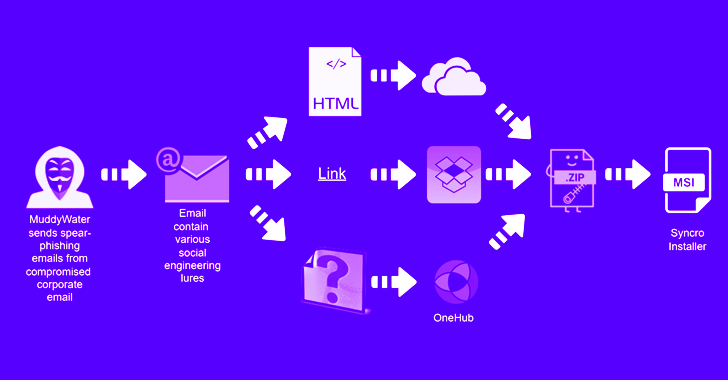
"The campaign has been observed targeting Armenia, Azerbaijan, Egypt, Iraq, Israel, Jordan, Oman, Qatar, Tajikistan, and the United Arab Emirates," Deep Instinct researcher Simon Kenin said in a technical write-up.
MuddyWater , also called Boggy Serpens, Cobalt Ulster, Earth Vetala, Mercury, Seedworm, Static Kitten, and TEMP.Zagros, is said to be a subordinate element within Iran's Ministry of Intelligence and Security (MOIS).
North Korean hackers exploited Internet Explorer zero-day to spread malware • TechCrunch

North Korean state-sponsored hackers exploited a previously unknown zero-day vulnerability in Internet Explorer to target South Korean users with malware, according to Google's Threat Analysis Group.
Google researchers first discovered the zero-day flaw on October 31 when multiple individuals uploaded a malicious Microsoft Office document to the company's VirusTotal tool.
Hackers Slaughter Samsung's Galaxy S22 On First Day Of Pwn2Own Competition | HotHardware
Little Rock School Board agrees to pay $250K to hackers
/cloudfront-us-east-1.images.arcpublishing.com/gray/SUY3WLWTC5EKTK2SWCVGNGEPTE.jpg)
LITTLE ROCK, Ark. (KARK/KAIT) – A central Arkansas school district is moving forward after hackers breached its system, holding critical information hostage.
According to content partner KARK , the Little Rock School Board publicly voted to approve a $250,000 ransom payment to the hackers on Tuesday, Dec. 6.
USB-C: Introduction For Hackers | Hackaday

We’ve now had at least five years of USB-C ports in our devices. It’s a standard that many manufacturers and hackers can get behind.
Modern devices have a set of common needs – they need a power input, or a power output, sometimes both, typically a USB2 connection, and often some higher-speed connectivity like a display output/input or USB 3. USB-C is an interface that aims to be able to take care of all of those.
Amnesty Canada says it was targeted by Chinese state-sponsored hackers • TechCrunch
The Canadian branch of Amnesty International has confirmed it was the target of a "sophisticated" cyberattack carried out by Chinese state-sponsored hackers.
Amnesty said there is no evidence that any donor or membership data was exfiltrated by the attackers, but Nivyabandi told TechCrunch that the threat actors had access to Amnesty’s working files.
5 Questions | 'Involve ethical hackers before using a software… reward them, work on their ...

Ritesh Pandey, BSP Lok Sabha MP from Ambedkar Nagar, Uttar Pradesh, tells Liz Mathew that the government needs to give serious attention to the threat of cyber attacks and have required laws and regulations in place
AIIMS is one of the most important medical centres in our country. The impact of the cyber attack was so severe that we could not control the servers and could access the data after many days. This issue needs our serious attention.
Hackers can impersonate, steal soldiers' identities - Israel News - The Jerusalem Post
Overshadowed by failures, crypto hacking exacts higher price - Roll Call

The cryptocurrency industry is circling the wagons in defense as hackers siphon more money from the sector each year.
Hackers made off with more than $3 billion in digital assets so far this year, according to research firm Chainalysis. In October alone, $718 million was taken in 11 different hacks, making it the worst month in the worst year for crypto hacking, the firm said.
Microsoft's Warning About How Hackers Are Bypassing MFA – What You Need to Know - Security Boulevard

With many companies shifting to multi-factor authentication (MFA) for verifying users, hackers have had to change their approach. Microsoft recently issued a warning that threat actors are gaining ground by adapting their techniques to bypass MFA protections.
Today, many users access work resources from a personal device like a cell phone or home PC. These unmanaged devices are a prime target for token theft, a method increasingly used by hackers.
Iran-linked MuddyWater hackers on the prowl again, using compromised corporate email accounts to launch spear-phish… https://t.co/swlXyNqhXM TheHackersNews (from The Internet) Fri Dec 09 13:05:00 +0000 2022
🔺هکرهای وابسته به #جمهوری_اسلامی علیه اهدافی در مناطق مختلف جهان اقدام کردهاند ▪️یک #گروه_سایبری وابسته به نهادها… https://t.co/xjvW1Dnfp4 VOAfarsi (from District of Columbia, USA) Fri Dec 09 20:27:34 +0000 2022
A Concert Like No Other
Hop aboard a shuttle to Kepler-1649c. Be there to welcome new lifeforms into the universe. All passengers must have a verified event ticket. There are 10,000 tickets in circulation so no need to panic. Limited seating available per trip. There will be multiple flights each hour shipping off from the NORAD Space Port in Iceland.
Event tickets are non refundable & non transferable (except on the black market. Call Sal with questions.) An event ticket can be reused for up to 9900 yearly transactions.
No sandals allowed on flight. Adults only. Kittens must show a custodian's ID at the gate. You are not allowed to get married while aboard the shuttle. Please arrive early if you are wearing jeans.
NB: EVENT TICKETS CONTAIN A PRIVATE ANONYMOUS DIGITAL IMPRINT.
Reserve your spot. Click here.

No comments:
Post a Comment