
North Korean state-sponsored hackers exploited a previously unknown zero-day vulnerability in Internet Explorer to target South Korean users with malware, according to Google's Threat Analysis Group.
Google researchers first discovered the zero-day flaw on October 31 when multiple individuals uploaded a malicious Microsoft Office document to the company's VirusTotal tool.
Researchers Uncover Darknet Service Allowing Hackers to Trojonize Legit Android Apps
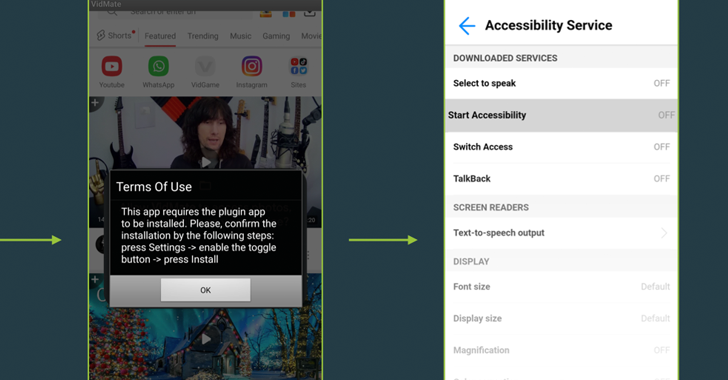
The ERMAC infections commence with a fraudulent website that claims to offer Wi-Fi authorization software for Android and Windows that, when installed, comes with features to steal seed phrases from crypto wallets and other sensitive data.
ThreatFabric said it also found a number of malicious apps that were trojanized versions of legitimate apps like Instagram, with the operators using them as droppers to deliver the obfuscated malicious payload.
Iranian Hackers Strike Diamond Industry with Data-Wiping Malware in Supply-Chain Attack
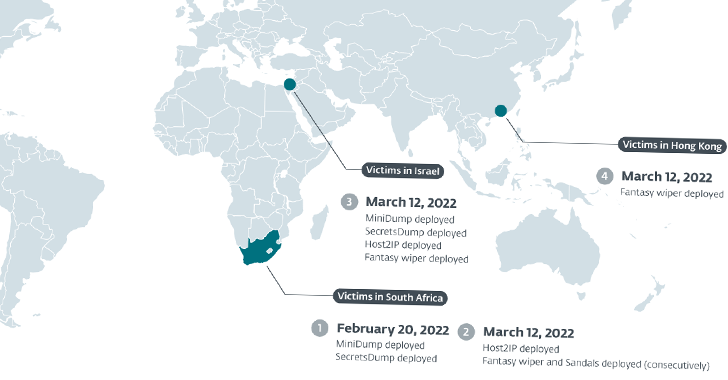
An Iranian advanced persistent threat (APT) actor known as Agrius has been attributed as behind a set of data wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong.
The wiper, referred to as Fantasy by ESET, is believed to have been delivered via a supply-chain attack targeting an Israeli software suite developer as part of a campaign that began in February 2022.
Russian Hackers Spotted Targeting U.S. Military Weapons and Hardware Supplier
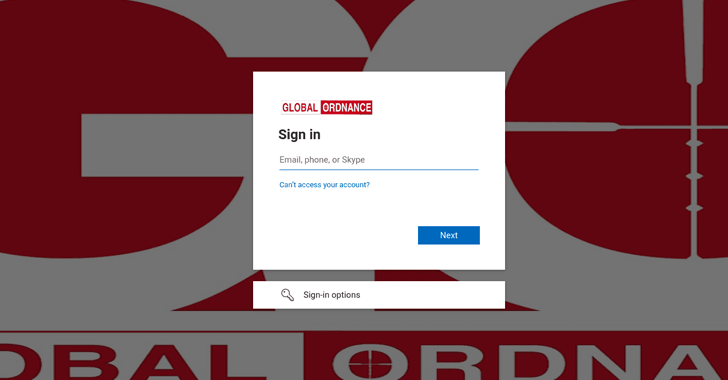
Recorded Future attributed the new infrastructure to a threat activity group it tracks under the name TAG-53 , and is broadly known by the cybersecurity community as Blue Callisto , Callisto, COLDRIVER, SEABORGIUM, and TA446.
"Based on historical public reporting on overlapping TAG-53 campaigns, it is likely that this credential harvesting activity is enabled in part through phishing," Recorded Future's Insikt Group said in a report published this week.
Apple's new Advanced Data Protection brings more security and encryption to iCloud - Vox

Apple, the company whose CEO is fond of calling privacy a human right , has added a few new privacy features to its devices. One of them, Advanced Data Protection, is adding end-to-end encryption to almost every iCloud service out there.
The company announced the update on Wednesday , although the upgraded encryption won't be available until the end of this year for US users and early next year for everyone else. When it does roll out, you'll have to choose to enable it in your iCloud settings.
Microsoft says hackers are using Telegram to connect with, hack VIPs at cryptocurrency companies ...

Threat actors have been directly targeting cryptocurrency investment companies using Telegram chat groups.
According to a new blog from Microsoft, a hacking group being tracked under the designation DEV-0139 has been using Telegram groups to facilitate communication between VIP clients and cryptocurrency exchange platforms, drawing their targets from among the members.
Chinese Hackers Using Russo-Ukrainian War Decoys to Target APAC and European Entities

Mustang Panda is a prolific cyber-espionage group from China that's also tracked under the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.
It's believed to be active since at least July 2018, per Secureworks' threat profile , although indications are that the threat actor has been targeting entities worldwide as early as 2012.
How to Prevent Against Increasingly Personalized Attacks From Hackers
"I put myself in the shoes of someone I want to hack and try to craft something specific to them," Snow said.
With the rapid migration to the cloud and increase in hybrid and remote work, we're seeing that greater flexibility also presents new vulnerabilities. According to the Cost of a Data Breach Report 2022, by Ponemon Institute and sponsored by IBM, 45% of data breaches occurred in the cloud.
Web skimming hackers infiltrate over 40 ecommerce websites - that we know of | TechRadar

In a blog post (opens in new tab) , the company outlined how it detected a web skimming attack on a discounted web marketing and analytics service occurred through the acquisition of its domain name (Cockpit). The domain name has not been in use since 2014.
The Group X skimmers were able to compromise over 40 ecommerce websites (opens in new tab) , and the data collected from the sites was encoded, encrypted and sent to an exfiltration server based in Russia, according to Jscrambler.
Russian Hackers Use Western Networks to Attack Ukraine - Infosecurity Magazine

Russian hackers are using their presence inside the networks of organizations in the UK, US and elsewhere to launch attacks against Ukraine, a new report from Lupovis has revealed.
The Scottish security firm set up a series of decoys on the web to lure Russian threat actors so it could study their tactics, techniques and procedures (TTPs).
More 0day in the wild, this time from North Korea targeting Internet Explorer from @_clem1 and @benoitsevens in TAG… https://t.co/Nq8oQqe3Ha ShaneHuntley (from Sunnyvale, CA) Wed Dec 07 16:13:37 +0000 2022
North Korean hackers exploited the Itaewon crowd surge tragedy to target South Koreans with malicious malware, says… https://t.co/mBx7SNpkVw GalloVOA (from Seoul, Republic of Korea) Thu Dec 08 00:08:04 +0000 2022
https://sypuber.page.link/reddcct
REDACTED ID. Click here.

No comments:
Post a Comment