
Tesla has become, for many drivers, the face of electric vehicles in the United States. This comes with ups and downs — on one hand, a wide-ranging charging network; on the other, a series of bizarre glitches that periodically come to light.
In a Tweet , Synacktiv provided more information on one of the hacks. “After having finished their exploit in an hotel room, @ p0ly and @vdehors successfully compromised the Tesla Model 3 infotainment through bluetooth and elevated their privileges to root!” the company wrote.
Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers
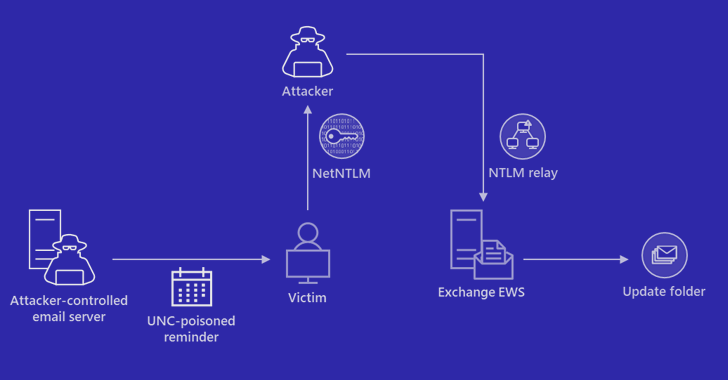
Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently patched Outlook vulnerability.
Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to a case of privilege escalation that could be exploited to steal NT Lan Manager (NTLM) hashes and stage a relay attack without requiring any user interaction.
Cybersecurity tech tips: 5 secrets only pros and hackers know

Some security steps are common knowledge. I don't need to remind you to install that latest update on your computer, right?
I always get calls to my national radio show from people concerned that someone is watching everything they do.
Maersk says posted data is not current and not from attack by hackers - The Loadstar

Maersk denies it has been cyber-attacked by hacker group Anonymous Sudan, despite leaked customer credentials appearing on social media.
"We have more data, this is just a sample," read the post, but Maersk says it is not obvious whether the data is current.
Introducing the new toy hackers are using that's worrying authorities - The Jerusalem Post
No comments:
Post a Comment