
The hackers who caused Colonial Pipeline to shut down on Friday began their cyberattack against the top U.S. fuel pipeline operator a day earlier and stole a large amount of data, Bloomberg News reported citing people familiar with the matter.
Holding tanks are seen at Colonial Pipeline's Charlotte Tank Farm in Charlotte, North Carolina, U.S. an undated photograph. Colonial Pipeline/Handout via REUTERS
Reuters, the news and media division of Thomson Reuters, is the world's largest multimedia news provider, reaching billions of people worldwide every day. Reuters provides business, financial, national and international news to professionals via desktop terminals, the world's media organizations, industry events and directly to consumers.
Cybersecurity warning: Russian hackers are targeting these vulnerabilities, so patch now | ZDNet

Russian cyber attacks are being deployed with new techniques - including exploiting vulnerabilities like the recent Microsoft Exchange zero-days - as its hackers continue to target governments, organisations and energy providers around the world.
It comes after cybersecurity agencies in the US and the UK attributed the SolarWinds attack to Russia's civilian foreign intelligence service , as well as several campaigns targeting Covid-19 vaccine developers .
SolarWinds: Hackers Accessed Our Office 365 Since Early 2019

Hackers persistently accessed SolarWinds’ internal systems, Microsoft Office 365 environment and software development environment for months before carrying out their vicious cyberattack .
The Austin, Texas-based IT infrastructure management vendor said hackers compromised SolarWinds’ credentials and conducted research and surveillance via persistent access for at least nine months prior to their October 2019 trial run. Hackers tested their ability to inject code into SolarWinds Orion network monitoring software in fall 2019, months before they actually started putting poisoned code into Orion.
How to tell if your passwords are vulnerable to hackers
To do this, log into your Google account on your laptop or desktop and then navigate to your account's home page. Select the Security tab and you should see a message at the top of the screen that says "Critical Security Issues Found."
The keys work with a number of major apps and websites including Google and Facebook, though banking apps may not support them — which is a bummer considering they're some of the most important apps to protect. But if you're looking for some serious security, such keys can go a long way.
How to Protect Yourself against Hackers During COVID-19 Lockdown?

As much as the large-scale adoption of technology sounds beneficial, it becomes more dangerous for an individual with no or limited knowledge of cybersecurity and the risks it brings. It is visible with during the lockdown. Hackers are targeting the first-time user connecting to the internet during the lockdown. Therefore, it is essential to improve your security. This blog will help an individual find out how to secure yourself and your company against cyberattacks during the lockdown.
Facebook hackers lock local women out of accounts | News Headlines | kmov.com

Multiple St. Louis women say a stranger took over their Facebook accounts, leaving them with no way to regain control of their posts and memories.
Watch out for hackers, Britain's spy agency tells smart cities | Reuters

Criminals and foreign governments can target technologies deployed to improve city services such as sensors and internet-connected devices to steal sensitive data and cause disruption, said Britain's National Cyber Security Centre (NCSC).
From sensors monitoring pollution to traffic lights designed to cut congestion, technology can help cities cut planet-warming emissions and make services more efficient, the NCSC said, as it published new cyber security guidance for local authorities.
AI consumes a lot of energy. Hackers could make it consume more. | MIT Technology Review

The news: A new type of attack could increase the energy consumption of AI systems. In the same way a denial-of-service attack on the internet seeks to clog up a network and make it unusable, the new attack forces a deep neural network to tie up more computational resources than necessary and slow down its "thinking" process.
The target: In recent years, growing concern over the costly energy consumption of large AI models has led researchers to design more efficient neural networks. One category, known as input-adaptive multi-exit architectures, works by splitting up tasks according to how hard they are to solve. It then spends the minimum amount of computational resources needed to solve each.
How to use authenticator apps like Google Authenticator to protect yourself online - Vox
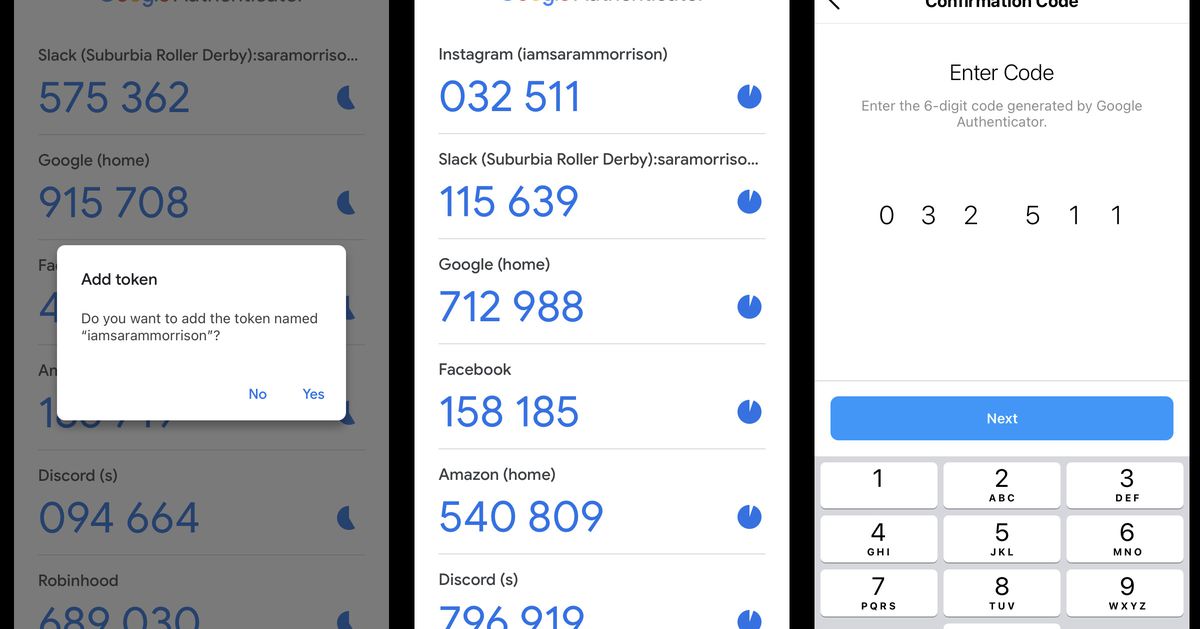
If you're using texts for two-factor authentication, it's time to change to an app. Here's what you need to know.
Text-based 2FA, where a text with a six-digit code is sent to your phone to verify your identity, is better known and better understood because it uses technology most of us use all the time anyway. But it's a technology that wasn't meant to serve as an identify verifier, and it's an increasingly insecure option as hackers continue to find ways to exploit it.
Flaw in Qualcomm modems enables backdoor for hackers to record your phone calls - comments
Hh, 23 hours ago Proud exinos/kirin user. Considering Samaung also like MediaTek dont release source code, it could have multiple backdoors if like the US Government wants to spy on certain individual. Kirin is banned so nvm.
Yeah well that's the problem when you only offer your clients 1 or 2 software updates. One can't just depend on the security patches to help. Oh well you get what you ask for. Not to be funny but surely in 2021 this problem can be sorted out. Or is android again just we don care.
Happening on Twitter
A criminal group originating from Russia named "DarkSide" is believed to be responsible for a ransomware cyberattac… https://t.co/ONnIswGX04 kaitlancollins (from Washington, D.C.) Mon May 10 01:43:15 +0000 2021
We are aware of the Colonial Pipeline ransomware incident. We are engaged with Colonial and our interagency partner… https://t.co/Q1KDzP5CQi CISAgov (from Washington, DC) Sat May 08 20:14:07 +0000 2021
A cyberattack forced Colonial Pipeline, the operator of one of the US' largest pipelines, to temporarily suspend op… https://t.co/j5Ev3wD4oU cnnbrk (from Everywhere) Sat May 08 14:42:45 +0000 2021

No comments:
Post a Comment