
Tech blog Bleeping Computer spotted reports yesterday that multiple distributed denial of service — a type of attack that overwhelm a server by flooding it with junk traffic — had disrupted alcohol sellers' access to a portal used by the Russian government to coordinate distribution of ...
Security researchers: Here's how the Lazarus hackers start their attacks | ZDNet

Liam Tung is a full-time freelance technology journalist who writes for several Australian publications.
The Lazarus hacking group is one of the top cybersecurity threats from North Korea, recently catching the attention of the US government for massive cryptocurrency heists.
Hackers are using trusted company names in scams
/cloudfront-us-east-1.images.arcpublishing.com/gray/6W4AM2PTTFDD7KN54ZI4QVKC2U.bmp)
"Not realizing it didn't have a Norton's logo or letterhead. I acted out of 'Hmm how dare they.' because it was more than I had paid the last year," she said.
"This guy's name was Steve and he sounded like he could have been my grandson - calling from Dallas. 'We are looking out for you Ms. Estelle. We are looking out for you, but please don't notify anybody.'"
US Sanctions Cryptocurrency 'Mixing' Service for Aiding North Korean Hackers | PCMag

The sanctions target Blender.io, a website that charges to “anonymize bitcoin transactions” by mixing it with funds from other users.
In addition, the US Treasury Department is signaling it’ll go after other cryptocurrency mixing services that are found helping hackers. The sanctions against Blender.io essentially outlaw US persons and groups from conducting any business with the cryptocurrency service.
Hackers Using PrivateLoader PPI Service to Distribute New NetDooka Malware
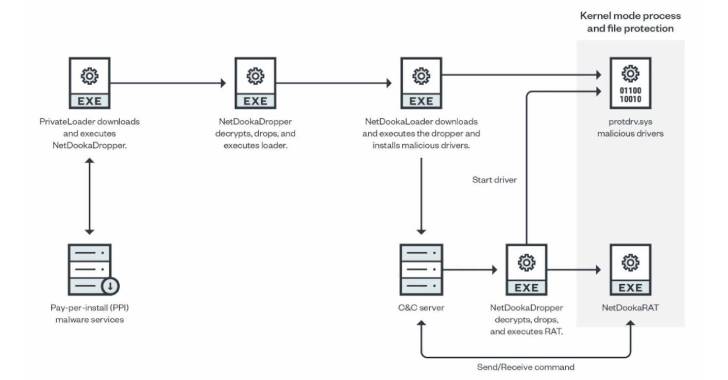
A pay-per-install (PPI) malware service known as PrivateLoader has been spotted distributing a "fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices.
"The framework is distributed via a pay-per-install (PPI) service and contains multiple parts, including a loader, a dropper, a protection driver, and a full-featured remote access trojan (RAT) that implements its own network communication protocol," Trend Micro said in a report published ...
Just Sayin': Hackers will try anything to get your money | Mineral County WV News and Tribune | ...

"Hello, can you help me? I got a new phone and can't log into my Facebook. Can you help me get a code so I can log on?"
Nothing about those words seems very alarming, especially since the request came to you from a friend. Yet in this day and age it is really hard to tell friend from foe, because who you think is your friend may turn out to be a hacker trying to gain access to your Facebook account.
Why Hackers Target Critical Infrastructure and Why It's Difficult to Upgrade Cybersecurity

In a recent 2022 Pwn2Own ethical hacking competition, two security researchers breached ICONICS Genesis64, a software designed for operators to use industrial machines, in mere seconds. In contrast, it took them three weeks to hack an iPhone way back in 2012.
Considering that major, multimillion-dollar companies and industries own these apps, many are surprised to learn how it's much easier to attack than most modern smartphones.
Instagram hacking: why is the art world a target—and how do you get your account back?

Hackers are attracted to accounts that enjoy a high level of engagement, such as those belonging to creatives
Insta' gratification is a monthly blog by Aimee Dawson, our acting digital editor. Looking at how the art world and Instagram collide, each article tackles a topic around the innovations and challenges that spring up when art enters the digital world.
Heroku confirms user details were stolen by hackers | TechRadar

Cloud application platform Heroku has confirmed that the recent cybersecurity incident, in which GitHub integration OAuth tokens were stolen, has led to further compromise, and ended up with customer credentials being stolen.
The database Heroku is referring to, according to a person previously affiliated with the company, is most likely "core-db”, BleepingComputer found.
Russian hackers coordinated latest missile strikes on Odesa

"Odesa was attacked by Russian invaders, again. According to Operational Command South, the enemy deployed strategic warplanes to launch cruise missiles. At about the same time, calls were posted on hostile platforms for a cyber attack on the Odesa City Council's website," the statement said.
#Google's Threat Analysis Group (TAG) says state-backed hackers and cybercriminals from China, Iran, North Korea an… https://t.co/fGFY0uPNGi TheHackersNews (from The Internet) Wed May 04 08:40:55 +0000 2022
System Unknown NFT Collection
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/systemunknown
Check out the System Unknown artwork. Click here.

No comments:
Post a Comment