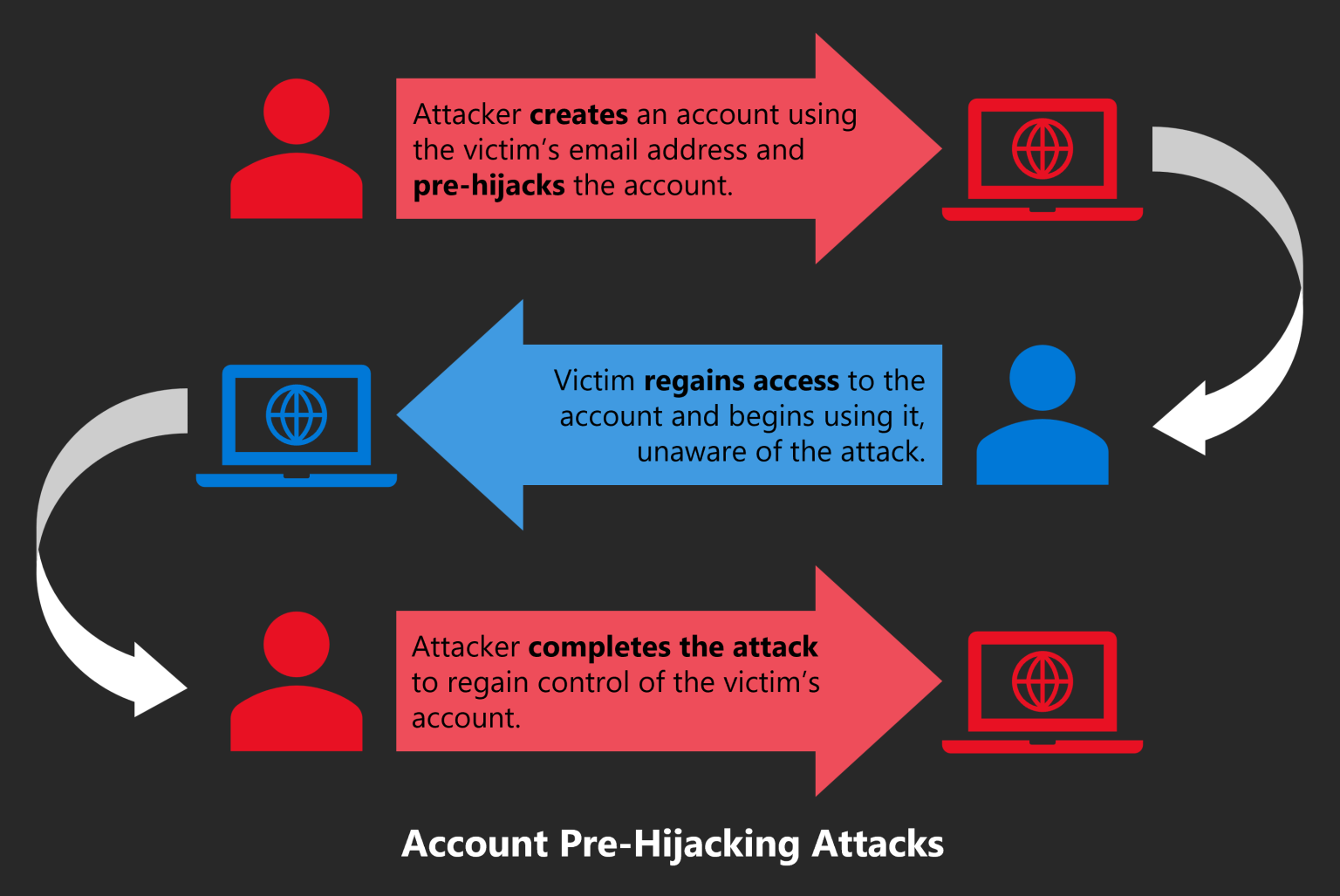
Pre-hijacking attacks take place in three stages, according to a recent Microsoft report (Credit: Microsoft Security Response Center) A recent report from Microsoft's Security Response Center identifies five different ways such accounts can be hacked, with the distinguishing feature ...
The Mystery of China's Sudden Warnings About US Hackers | WIRED

Since the start of 2022, China's Foreign Ministry and the country's cybersecurity firms have increasingly been calling out alleged US cyberespionage. Until now, these allegations have been a rarity.
"These are useful materials for China's tit-for-tat propaganda campaigns when they faced US accusation and indictment of China's cyberespionage activities," says Che Chang, a cyber threat analyst at the Taiwan-based cybersecurity firm TeamT5.
Hackers Breached Some GM Accounts, Accessing Personal Data

Hackers compromised some online accounts of General Motors Co. customers in April, potentially accessing addresses, phone numbers and other personal information, according to a data breach notice filed with California regulators.
In a letter to affected customers, GM said it identified suspicious login attempts to an unspecified number of accounts between April 11 and April 29. The intrusions allowed hackers in some cases to redeem gift cards using reward points.
Hackers Increasingly Using Browser Automation Frameworks for Malicious Activities
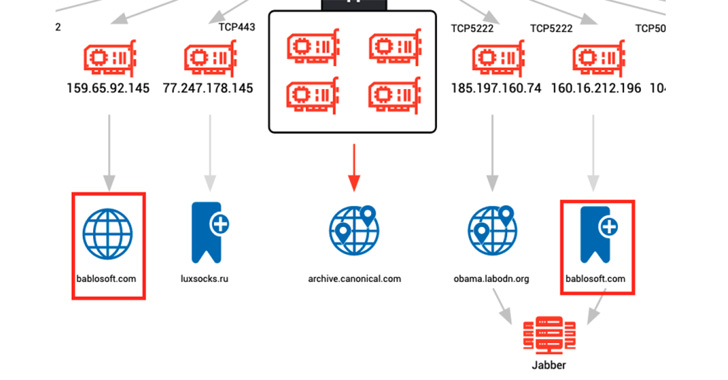
"The framework contains numerous features which we assess may be utilized in the enablement of malicious activities," researchers from Team Cymru said in a new report published Wednesday.
"The technical entry bar for the framework is purposefully kept low, which has served to create an active community of content developers and contributors, with actors in the underground economy advertising their time for the creation of bespoke tooling."
Relief for White Hat Hackers and Web Scrapers? | McDermott Will & Emery - JDSupra

DISCLAIMER: Because of the generality of this update, the information provided herein may not be applicable in all situations and should not be acted upon without specific legal advice based on particular situations.
Here's What Hackers Are Really Doing With Your Info

Consumers often react to the risk of being hacked in two ways: by either being extra cautious or dismissing the risk outright by saying, "It won't happen to me.
F1 Solutions explains what hackers are really doing with your data: selling it, exposing it, holding it for ransom, mining it for valuable info like credit card numbers, using it for other hacks, or simply showing it off.
ShardSecure aims to make sensitive cloud data unintelligible to hackers  | SC Media

Cisco-451 Research study says 82% of respondents have adopted a hybrid cloud strategy, with 58% moving data between on-premises and public cloud environments weekly.
A new CRA survey found that roughly half of respondents have serious concerns about securing cloud workloads, even as their organizations march forward with cloud-first strategies.
Smart Farm Technology Open to Hackers – WOWO 1190 AM | 107.5 FM

Experts say it's important to realize that modern farm technology is vulnerable to attacks by hackers, which could leave the supply chain exposed to further risk.
Hackers steal 29 Moonbirds valued at $1.5 million in NFT phishing attack

Late Tuesday, 29 Moonbirds valued at about 750 ETH ($1.5 million) were taken from their owner, DigitalOrnithologist , according to on-chain data.
Despite having only launched a month ago, Moonbirds are quickly joining the Bored Ape Yacht Club as a popular target for hackers.
Hackers target Windows security experts with fake exploits | TechRadar

Cybersecurity researchers, analyzing proof-of-concept (PoC) exploits published on GitHub, recently found themselves on the receiving end of a Cobalt Strike-powered cyberattack.
It’s common practice for researchers to publish a PoC of recently patched flaws on code repositories, such as GitHub. That way, they can test different solutions among themselves and force admins to apply the fixes as soon as possible.
We love trees 🥰🍀💕❤️💋😘
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/aotam
Hot NFT tree art collection available. This is BIG!
See the amazing artwork. Click here.

No comments:
Post a Comment