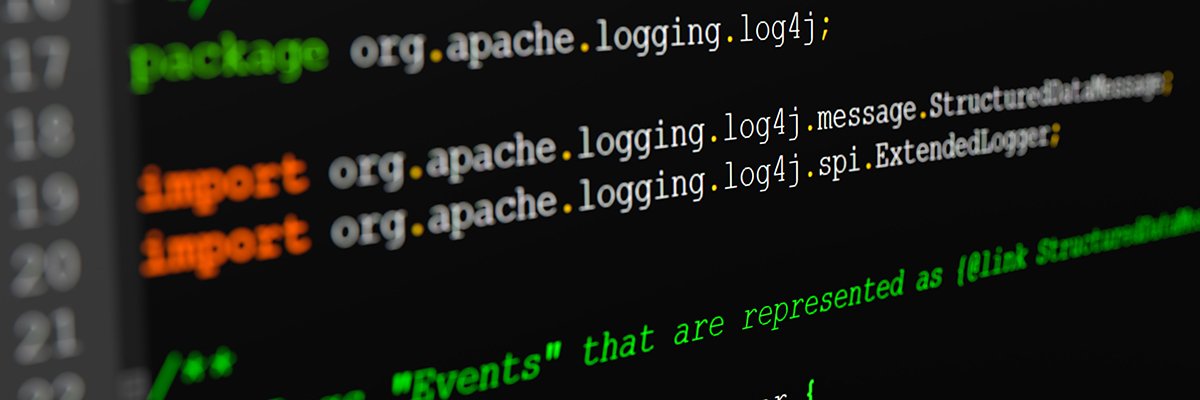
Imagine the scene: a severe vulnerability emerges that affects organisations worldwide, allowing unauthorised access to highly sensitive data. This scenario happened in late 2021 when a popular open source tool published a critical vulnerability called Log4Shell.
So, what exactly happened? Log4Shell is a software vulnerability found in Apache Log4j, a widely used Java library for logging error messages in applications. It sent organisations into panic mode as they scrambled to discover if they were vulnerable.
Hackers Found Selling Stolen University Credentials

The logins, harvested through spear-phishing, ransomware, or other tactics, are reportedly being sold on both online criminal marketplaces and publicly accessible forums.
And as of January 2022, Russian cybercriminal forums were offering the network credentials and virtual private network accesses to universities and colleges across the US, some of which included screenshots as proof of access. Prices varied from a few dollars to several thousand.
JBS Foods cyber attack highlights industry vulnerabilities to Russian hackers - ABC News
Australia's food supply is uniquely vulnerable to cyber attacks, the director of a national cybersecurity firm warns, as he calls for the industry to raise its standards on the anniversary of the JBS ransomware hack.
JBS Foods, the world's biggest meat processor, was held ransom by Russian-based hackers for $US11 million last year.
Hackers' Phishing Attack Cuts Off Moonbirds NFTs Worth $1.5 Million | Bitcoinist.com

Hackers could turn Windows Subsystem for Linux into a secret weapon | TechRadar

Windows Subsystem for Linux (WSL) is becoming a breeding ground for malware , cybersecurity researchers are saying.
While WSL-based malware is not particularly new (spotted as early as September 2021), it’s been rising in popularity among cybercriminals of late.
Liam Gallagher blames hackers for false Manchester gig cancellation rumour

Liam Gallagher has blamed hackers for editing his website to announce falsely that his Manchester show at the Etihad Stadium had been cancelled.
The soloist and former Oasis frontman took to Twitter over the weekend to tell fans that his headline show was still on. “I hear some [bell]end has hacked my official website saying that the MANCHESTER gig is cancelled it's not see ya there MCFC CHAMPIONS OF ENGLAND,” he wrote.
Car hackers target internet-connected vehicles: Tips to stop them | Express.co.uk

Mr Fulthorpe said: “By 2026 all cars sold in the UK are expected to be connected to the internet.
“As exciting and as innovative as this sounds, it also means additional vulnerabilities which hackers will be able to exploit.
“We have already seen an increase in keyless motor theft where hackers use a relay box to boost the signal from car keys to gain entry.
Ringo Presents Soul Hackers 2 May 30th Daily Demon; Ringo's Technical Sister & Fellow ...
![]()
Atlus Japan has begun a new series on its Youtube channel where the protagonist of the upcoming Soul Hackers 2 , Ringo, introduces demons that will appear in the title.
Today’s Demon of the D–wait, what? Where did it go? Oh, I see a silhouette. It’s…oh, it’s Figue.
World governments and paid hackers, the main source of newly discovered Android exploits - Royals ...

In case anyone was wondering, most of the newly discovered software vulnerabilities and malware used to attack computer systems are being developed by law enforcement agencies and with the funding of governments fighting in the online space.
The exact amounts paid are not known, but we find out that the respective groups of hackers have carried out numerous attacks in countries other than their home countries.
New WhatsApp OTP Scam Allows Scammers to Hijack Your Account

On May 23rd, 2022, the founder and CEO of CloudSEK, a contextual AI firm, Rahul Sasi, shared details of a new WhatsApp scam where threat actors try to hijack users’ accounts through phone calls.
“First, you receive a call from the attacker who will convince you to make a call to the following number **67*<10 digit number> or *405*<10 digit number>. Within a few minutes, your WhatsApp would be logged out, and the attackers would get complete control of your account.
Army of the Alien Monkeys
Earth is nice. We want it.
We welcome your submission to us.


No comments:
Post a Comment