
The Microsoft Word vulnerability first began to receive widespread attention on May 27th, when a security research group known as Nao Sec took to Twitter to discuss a sample submitted to the online malware scanning service VirusTotal.
In a blog post published on May 29th, researcher Kevin Beaumont shared further details of the vulnerability.
Okta's Fearful Cyber Response Worse Than Hackers' Peek—How 3 Tempting Tech Crisis Shortcuts Cost ...

Regardless of precautions and incident plans, cyberattacks terrify C-suites. The recent identity-security firm Okta breach spotlights a common leadership response mistake — sacrificing customer trust for overestimated legal risk.
In January 2022, hacker group LAPSUS$ infiltrated an Okta contractor's computer. Relying on its vendor's initial forensics, Okta opted not to disclose the brief attack. The breach was eventually made public in March via a series of hacker posts.
Zhang lab takes on cyber-physical system hackers - The Source - Washington University in St. Louis

When it comes to computer security, there are three main objectives: confidentiality — ensuring no one can steal your data; integrity — ensuring that your data has not been changed in any unauthorized way; and availability — making sure that you have access to the resources you need to do ...
New Unpatched Horde Webmail Bug Lets Hackers Take Over Server by Sending Email
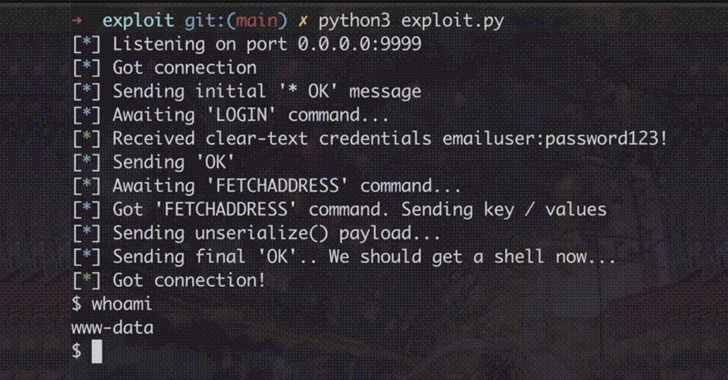
The issue, which has been assigned the CVE identifier CVE-2022-30287 , was reported to the vendor on February 2, 2022. The maintainers of the Horde Project did not immediately respond to a request for comment regarding the unresolved vulnerability.
At its core, the issue makes it possible for an authenticated user of a Horde instance to run malicious code on the underlying server by taking advantage of a quirk in how the client handles contact lists.
Hackers ransom 1,200 exposed Elasticsearch databases

A mass hijacking of unsecured cloud instances has led to some 1,200 databases being held for ransom by threat actors.
"While the threat actor could have used a tool like Elasticdump to exfiltrate the data, the cost of storing data from 1,200 databases would be prohibitively expensive," the CTU researchers explained in a blog post Wednesday.
Manufacturing has become most popular target of hackers, says TXOne Networks

TXOne Networks CEO Terence Liu speaks at the 2021 Hacks in Taiwan Conference. Credit: TXOne Networks
Bolstering operational technology (OT) security is a budding awareness among semiconductor suppliers, as the manufacturing industry has become the most popular target of hackers, according to Terence Liu, CEO of TXOne Networks.
Medium-Range Rockets and Hackers Signal Escalating US Support to Ukraine | Military.com

The U.S. military is stepping up its aid to Ukraine with high-tech medium-range rocket systems as part of a new $700 million shipment that also includes Javelins and Soviet-era helicopters, the Pentagon said Wednesday.
The decision to send the rockets, which are used by the Army , comes as the head of U.S. Cyber Command, Gen. Paul Nakasone, told a U.K. news outlet Wednesday that U.S.
Pleased to have signed this cross-party letter calling for an audit of UK assets held by Hong Kong officials who ar… https://t.co/UA4FASROuy BarrySheerman (from Huddersfield) Tue May 31 16:01:37 +0000 2022
There was 'no' order for PPE kits from China as Claimed JCB industries could not fulfil 'urgent orders' for PPE ki… https://t.co/P8f2icuCXJ manoranjanpegu Thu Jun 02 06:51:50 +0000 2022
We love trees 🥰🍀💕❤️💋😘
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/aotam
Hot NFT tree art collection available. This is BIG!
See the amazing artwork. Click here.

No comments:
Post a Comment