
Hackers can get into these popular smart home gadgets

Even though they are made by two of the largest technology companies in the world, it doesn't mean they can't be hacked. A research group recently found that many older models are no longer secure.
U.K.-based consumer products website Which? conducted tests on several smart home gadgets and found that many can leave you vulnerable to hackers. The study highlights the importance of updating your technology regularly.
Hackers take control of Facebook accounts posting sexually explicit images and fraud charges - ...

Hackers Exploiting Unpatched Critical Atlassian Confluence Zero-Day Vulnerability

Atlassian has warned of a critical unpatched remote code execution vulnerability impacting Confluence Server and Data Center products that it said is being actively exploited in the wild.
The Australian software company credited cybersecurity firm Volexity for identifying the flaw, which is being tracked as CVE-2022-26134 .
Microsoft Blocks Iran-linked Lebanese Hackers Targeting Israeli Companies

The adversarial collective is believed to have breached more than 20 organizations based in Israel and one intergovernmental organization with operations in Lebanon since February 2022.
Targets of interest included entities in the manufacturing, IT, transportation, defense, government, agriculture, financial, and healthcare sectors, with one cloud service provider compromised to target a downstream aviation company and law firm in what's a case of a supply chain attack.
Secrets in code make passwords vulnerable to hackers | Security Magazine

Whether stored in a public or private code repository, hackers can target enterprise secrets and find PII and other organizational secrets.
The "Secrets Insights Across the Software Supply Chain'' report from Apiiro analyzed over 25,000 repositories ranging from small to large organizations to discover the state of secrets in today's code.
Chinese LuoYu Hackers Using Man-on-the-Side Attacks to Deploy WinDealer Backdoor
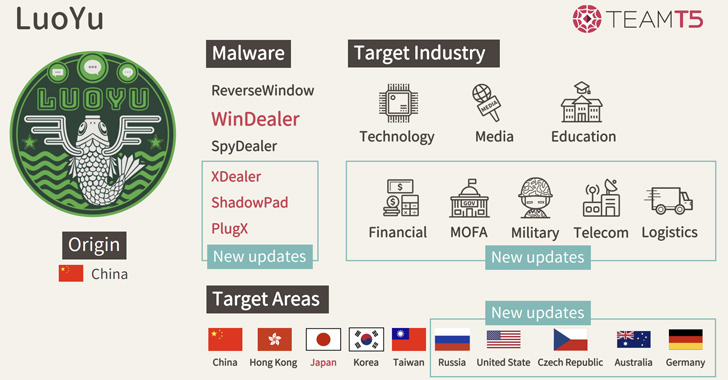
An "extremely sophisticated" Chinese-speaking advanced persistent threat (APT) actor dubbed LuoYu has been observed using a malicious Windows tool called WinDealer that's delivered by means of man-on-the-side attacks.
"This groundbreaking development allows the actor to modify network traffic in-transit to insert malicious payloads," Russian cybersecurity company Kaspersky said in a new report.
Hackers apparently lack honesty

Health care is a regular target of ransomware , with 66% of organizations surveyed saying they were hit with ransomware last year, up 34% from 2020.
What do these organizations get back when they pay? The survey shows not as much as they hoped. Those paying only received 65% of their data in 2021, down from 69% in 2020.
Hackers could disrupt millions of smartphones by abusing this critical bug | TechRadar

Security analysts from Check Point Research (CPR) found the flaw in the UNISOC modem which, as the researchers claim, can be found in 11% of all the smartphones in the world (predominantly in Africa and Asia).
The modem allows for cellular communication, and by leveraging the flaw, the attacker can remotely deny modem services and block communication.
Soul Hackers 2 for PS5, PS4, Xbox, & PC Reveals Decarabia With New Trailer

Today Atlus released another daily trailer of its upcoming JRPG Soul Hackers 2, focusing on one of the demons that will appear in the game.
We take a look at Decarabia, a demon that has been around in the Shin Megami Tensei series and also recently appeared in Shin Megami Tensei V .
US confirms for first time it helps Ukraine conduct cyberattacks -General Paul Nakasone He said US was conducting… https://t.co/hagn1SM3r5 EuromaidanPress Thu Jun 02 02:30:00 +0000 2022
Escaped inmate Gonzalo Lopez captured, Leon County Sheriff's Office confirms https://t.co/vapPx4MACZ MSN (from Redmond, WA, USA) Fri Jun 03 03:36:38 +0000 2022
We love trees 🥰🍀💕❤️💋😘
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/aotam
Hot NFT tree art collection available. This is BIG!
See the amazing artwork. Click here.

No comments:
Post a Comment