
A Chinese advanced persistent threat (APT) known as Gallium has been observed using a previously undocumented remote access trojan in its espionage attacks targeting companies operating in Southeast Asia, Europe, and Africa.
Called PingPull , the "difficult-to-detect" backdoor is notable for its use of the Internet Control Message Protocol ( ICMP ) for command-and-control (C2) communications, according to new research published by Palo Alto Networks Unit 42 today.
How Employees Can Invite Hackers into Your Network - My TechDecisions

The new working environment has challenges for organizations and employees. According to Gartner, the worldwide information security market is predicted to hit $170.4 billion in 2022.
However, smart companies know that most savings will come from employee sensitization. Cybint reports that 95% of cybersecurity attacks are caused by human error. Therefore, the most effective way to keep hackers out of your network is by teaching your employees how they're inviting them in.
Hackers Gonna Hack: Cyber Defense Not the Only Way to Shake 'Em Off - ClearanceJobs

Ransomware attacks against municipalities have steadily increased in recent years, and according to the 2022 Cyber Security Statistics report from PurpleSec, 48 of 50 U.S. states, as well as the District of Columbia, experienced at least one ransomware attack between 2013 and 2018.
One problem is that too often, organizations, agencies, and even communities are all too willing to pay the ransom.
Chinese Hackers Distribute Backdoored Web3 Wallets for iOS and Android Users
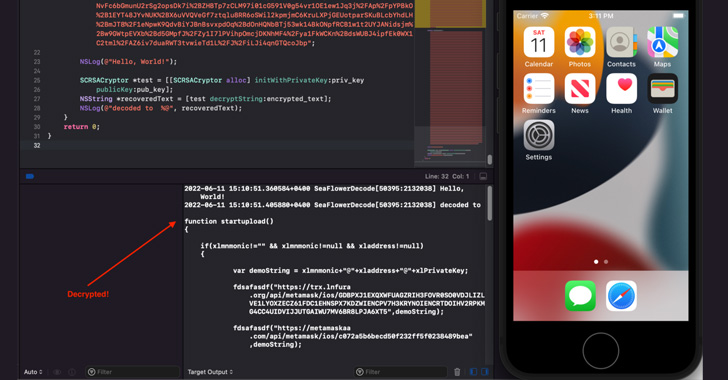
"As of today, the main current objective of SeaFlower is to modify Web3 wallets with backdoor code that ultimately exfiltrates the seed phrase," Confiant's Taha Karim said in a technical deep-dive of the campaign.
Targeted apps include Android and iOS versions of Coinbase Wallet, MetaMask, TokenPocket, and imToken.
Iranian Hackers Spotted Using a new DNS Hijacking Malware in Recent Attacks

The Iranian state-sponsored threat actor tracked under the moniker Lyceum has turned to using a new custom .NET-based backdoor in recent campaigns directed against the Middle East.
"The new malware is a .NET based DNS Backdoor which is a customized version of the open source tool 'DIG.net,'" Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar said in a report published last week.
Russian hackers start targeting Ukraine with Follina exploits

Ukraine's Computer Emergency Response Team (CERT) is warning that the Russian hacking group Sandworm may be exploiting Follina, a remote code execution vulnerability in Microsoft Windows Support Diagnostic Tool (MSDT) currently tracked as CVE-2022-30190.
The security issue can be triggered by either opening or selecting a specially crafted document and threat actors have been exploiting it in attacks since at least April 2022.
Save Big On Soul Hackers 2 Preorders For PC - GameSpot

Soul Hackers 2 doesn't arrive until August 25, but this new deal makes it worthwhile to reserve your copy today. Here's a closer look at the discounts currently available at Fanatical:
All preorders include the exclusive Persona 5 Phantom Thieves Outfit Pack. Spring for the Deluxe edition and you'll get a Bonus Story Arc (Lost Numbers) and a Booster Item Pack.
Eight Zero Days Could Open Doors for Hackers - Infosecurity Magazine

Security researchers have revealed eight new zero-day vulnerabilities in an industrial control system (ICS) that could enable attackers to physically access nominally secure facilities.
The bugs were discovered in Carrier’s LenelS2 access control panels , manufactured by HID Mercury, which the vendor markets to small businesses up to large enterprises. They’re said to be popular across healthcare, education, transportation and government sectors.
New Tesla Key Card Vulnerability Lets Hackers Silently Steal Your Ride – Review Geek

It’s no secret that Tesla has endured its share of potential problems regarding hackers accessing vehicles . However, a new report out of Austria shows a big vulnerability with Tesla’s NFC key cards that could let a hacker add a new card, then steal your car.
Last year, Tesla issued several updates around the key cards to improve usage and security. The update made it easier to start a vehicle after unlocking the doors with the digital key card, as the key didn’t need to be placed in the center console to shift out of park and drive off.
Prophet row: International hackers launch series of cyber attacks on India against Nupur Sharma's ...

Following recent remarks by suspended BJP spokesperson, Nupur Sharma, about Prophet Muhammad, the Malaysia-based hacktivist group DragonForce has launched a series of cyber attacks against the Indian government.
Cyber experts predict that the intensity and volume of such attacks on Indian entities are only going to increase, and the government and enterprises should ensure adequate safety measures to secure their digital properties.
Chinese APT hackers known as "Gallium" have been spotted using a new remote access trojan, dubbed "PingPull," in th… https://t.co/xtJJEiIv23 TheHackersNews (from The Internet) Mon Jun 13 13:27:32 +0000 2022
Army of the Alien Monkeys
Earth is nice. We want it.
We welcome your submission to us.
No comments:
Post a Comment