In one example, hackers from Turkey created fake messages from Twitter in an effort to hijack users' accounts, according to the study from security software company Proofpoint.
The Turkish hackers have primarily targeted journalists with this technique in an effort to steal their social media accounts, according to the study.
These moonlighting hackers are using ransomware against 'random' targets | ZDNet

Microsoft has raised an alert over a ransomware gang that is apparently based in North Korea and has successfully compromised small business since September 2021.
Microsoft Threat Intelligence Center (MSTIC) is tracking the group as an emerging threat under the tag DEV-0530 and says the 'H0lyGh0st' payload has affected small businesses in multiple countries over the past year.
Security Obscurity Versus Ethical Hackers: Who's Right?

Security breaches can lead to damage to a business’s finances, operations and reputation. What many companies might fear most is the latter: damage to their reputation. This may explain why 65% of organizations want to be seen as infallible, as per a recent HackerOne survey .
The continued practice of security through obscurity is harmful. When a group denies vulnerability and does not seek help, it leaves the door open for damaging attacks. Still, it’s not easy to open up about your weaknesses. So, where does this leave the ethical hacker?
Flipkart’s Cleartrip confirms data breach after hackers put data for sale – TechCrunch

Cleartrip , one of the popular travel-booking platforms in India, has confirmed a data breach after hackers claimed to post the stolen data on the dark web.
Responding to a request for comment by TechCrunch based on a tip shared by a security researcher, Cleartrip said it is taking legal action against the hackers.
Hackers Distributing Password Cracking Tool for PLCs and HMIs to Target Industrial Systems
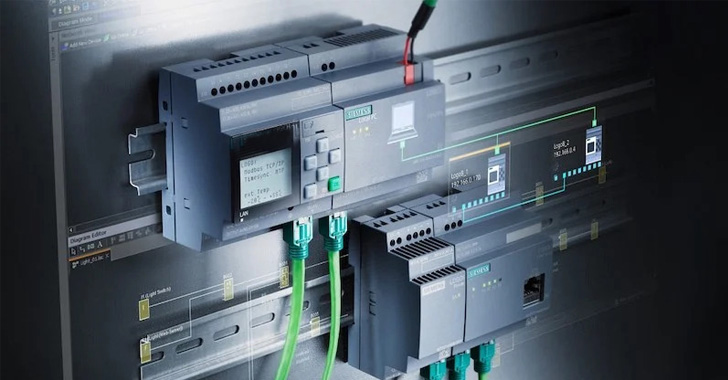
The exploit, tracked as CVE-2022-2003 (CVSS score: 7.7), has been described as a case of cleartext transmission of sensitive data that could lead to information disclosure and unauthorized changes. The issue was addressed in firmware Version 2.72 released last month.
What's more, the artifact unearthed by Dragos functions drops a crypto-clipper payload that steals cryptocurrency during a transaction by substituting the original wallet address saved in the clipboard with the attacker's wallet address.
Hackers steals $400K in NFTs from Premint users via malicious link

Blockchain security company Certik confirmed that the hackers stole 314 NFTs, which included NFTs from notable projects like Bored Ape, Goblintown, and Otherside.
– https://t.co/l3yEk2tUDs
– https://t.co/wdo7sJMia1
– https://t.co/8bBEgpKupN
– https://t.co/iY4tna437S
RaHDIt hackers single out Russian citizens working with Ukrainian intelligence – ThePrint ...
Moscow [Russia], July 18 (ANI/Sputnik): The RaHDIt Russian hacker group has handed over information on Russian citizens who have been collaborating with Ukrainian military intelligence to competent authorities, a RaHDIt member told Sputnik on condition of anonymity.
Earlier this month, RaHDit hackers leaked information on thousands of officers of Ukraine’s Main Directorate of Intelligence of the Ministry of Defense (GUR, or HUR).
Hackers on Planet Earth Conference | ... & Moring LLP

Hackers Steal $718M From Web 3 Attacks In Q2 2022: Report - Benzinga

According to a recent study by Web 3 security firm Beosin, over $718 million were lost to Web 3-related schemes during the second quarter of 2022.
The report says 48 major "attacks" were responsible for the losses incurred. Each accounted for over $100 million in losses, with 28 incurring losses of $1 million to $10 million.
Hackers can spoof commit metadata to create false GitHub repositories

Moreover, each commit boasts a unique hash or ID. Developers must remain cautious as threat actors can falsify some data from GitHub repositories to enhance their track record and make them appealing.
Researchers identified that a threat actor could tamper with commit metadata to make a repository appear older than it is. Or else, they can deceive developers by promoting the repositories as trusted since reputable contributors are maintaining them.
Hackers pose as Twitter employees, journalists in new breach tactics https://t.co/oQdoliWnCg https://t.co/MveDC8p8YA nypost (from New York, NY) Mon Jul 18 14:17:43 +0000 2022
Beware. Hackers pose as Twitter employees, journalists in new breach tactics https://t.co/bzmPiTwdnx via @nypost richsignorelli (from New York) Mon Jul 18 17:08:31 +0000 2022
Army of the Alien Monkeys
Earth is nice. We want it.
We welcome your submission to us.


No comments:
Post a Comment