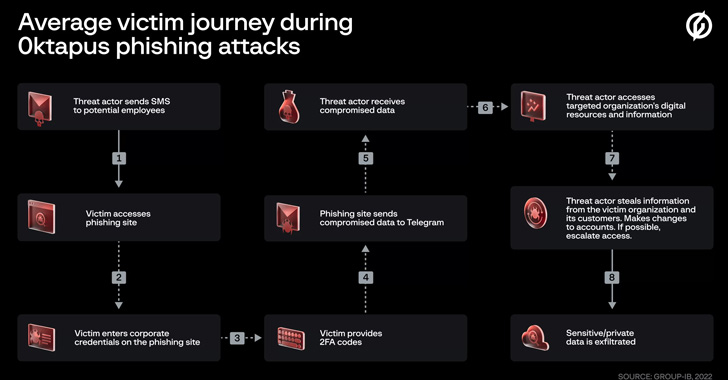
The activity has been condemned 0ktapus by Group-IB because the initial goal of the attacks was to "obtain Okta identity credentials and two-factor authentication (2FA) codes from users of the targeted organizations."
Calling the attacks well designed and executed, the Singapore-headquartered company said the adversary singled out employees of companies that are customers of identity services provider Okta.
DoorDash hit by data breach linked to Twilio hackers – TechCrunch
Food delivery giant DoorDash has confirmed a data breach that exposed customers’ personal information.
In a blog post shared with TechCrunch ahead of its publication at market close, DoorDash said malicious hackers stole credentials from employees of a third-party vendor that were then used to gain access to some of DoorDash’s internal tools.
Hackers may have breached medical billing records of nearly 1 million CNY patients - syracuse.com
Syracuse, N.Y. -- The medical billing records of nearly 1 million Central New York patients may have been obtained by hackers.
No private medical information, credit card numbers or Social Security numbers were exposed, said David Barletta, chief executive officer of Practice Resources. Practice Resources' required public notice said there was "no evidence that information was misused as a result of this incident.
Soul Hackers 2 Review: Stylish But Lacking

Soul Hackers 2 sees players trying to save the world with help from demons that the player can summon, but the futuristic turn-based role-playing game rarely rises above the sum of its parts.
The game starts off with players in the shoes of Ringo, a personified agent of Aion, which itself is essentially a giant, sentient, digital conglomerate.
Microsoft: Russian hackers gain powerful 'MagicWeb' authentication bypass | ZDNET

Microsoft has warned that the hacking group behind the 2020 SolarWinds supply chain attack have a new technique for bypassing authentication in corporate networks.
The trick, a highly specialized capability Microsoft calls "MagicWeb", allows the actors to keep a firm position in a network even as defenders attempt to eject them.
Hackers tapping cookies to gain entry into corporate networks - The Hindu BusinessLine

With services like malware-as-a-service solutions are available in the darknet, it has become easier for the hackers to quickly launch the attacks.
Remote desktop tool is hackers' dream | U.S. & World | gazette.com

A software tool designed to allow legitimate remote access to computer desktops has vulnerabilities that leave critical infrastructure operators open to cyberattacks, according to a cybersecurity company.
The virtual network computing tool , designed to allow remote desktop sharing, is often used in tech help-desk situations or when a computer user is traveling or wants to access a second computer in the house.
How 'Kimsuky' hackers ensure their malware only reach valid targets

The new safeguards implemented by Kimsuky are so effective that Kaspersky reports an inability to acquire the final payloads even after they are successfully connected to the threat actor’s command and control server.
At the same time, the visitor’s IP address is forwarded to the second-stage C2 server as a subsequent checking parameter.
LastPass Says Hackers Took 'Portions Of Source Code' | CRN

Okta Hackers behind the cyberattacks on #Twilio and #Cloudflare earlier this month have been linked to a broader ca… https://t.co/nCvO1bdAr1 TheHackersNews (from The Internet) Thu Aug 25 14:50:04 +0000 2022
We love trees 🥰🍀💕❤️💋😘
#NFT #ETH #nftgiveaways #nftcommunity #Giveaways #NFTPromotion #ART
https://opensea.io/collection/aotam
Hot NFT tree art collection available. This is BIG!
See the amazing artwork. Click here.


No comments:
Post a Comment